In 2019, a major financial services company, Capital One, experienced a severe security breach caused by a misconfigured API. This breach exposed the personal data of over 100 million customers, including sensitive information such as names, addresses, and social security numbers. The incident not only inflicted substantial financial and reputational damage on the company but also underscored the critical importance of securing APIs in today’s interconnected world.
APIs have become the backbone of modern cloud-native applications, enabling seamless communication and data exchange between various services. However, as reliance on these interfaces grows, securing them has become a paramount concern for developers and organizations alike. In the context of Amazon Web Services (AWS), a leading cloud platform, securing these endpoints is even more crucial due to the unique challenges and opportunities presented by the cloud environment.
This article aims to provide developers with a comprehensive guide on effectively securing APIs within an AWS ecosystem. We will explore best practices, common pitfalls, and advanced security measures specific to AWS, empowering you to build robust and secure API-driven applications. Whether you are new to securing web services or looking to enhance your existing knowledge, this article will equip you with the insights and tools necessary to navigate the complex landscape of API security in the cloud.
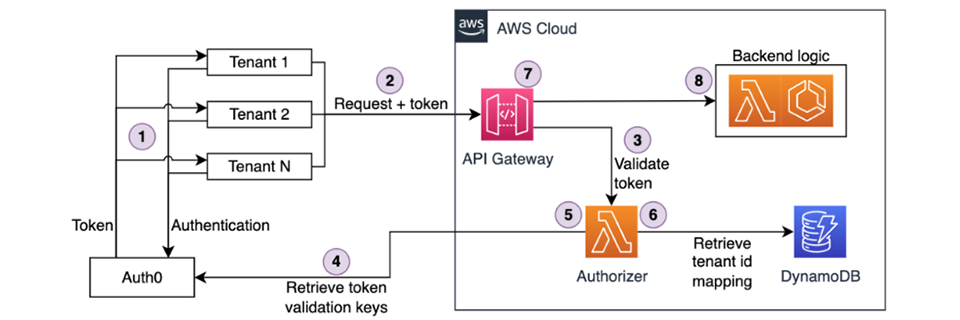
Understanding API Security
What is an API?
As you are probably aware, APIs (Application Programming Interfaces) are essential in enabling different software applications to communicate and exchange data. They act as intermediaries, allowing developers to tap into the functionality of various services or systems without needing to understand their underlying complexities.
In our interconnected digital world, you’ll have noticed that APIs are everywhere, from powering mobile apps to supporting enterprise systems. However, their widespread use also makes them attractive targets for malicious actors looking to exploit vulnerabilities and gain unauthorized access to sensitive data or systems.
Securing APIs is crucial, as a compromised API can lead to several serious issues:
- Data Breaches: Exposing sensitive user information, intellectual property, or confidential business data.
- System Disruption: Allowing attackers to manipulate or disrupt the functionality of applications that rely on the API.
- Reputational Damage: Eroding user trust and harming the organization's brand image in the event of a security incident.
In the context of AWS, securing APIs is even more vital due to the dynamic and scalable nature of cloud environments. Let’s explore the specific security challenges that arise when deploying APIs in the cloud.

Security Challenges in a Cloud Environment
When deploying APIs in an AWS cloud environment, several unique security challenges arise:
- Increased Attack Surface
Cloud environments inherently have a broader attack surface compared to traditional on-premises setups. The global accessibility of APIs means attackers have more entry points to target and exploit vulnerabilities. The vast interconnection of cloud services and resources further complicates the task of maintaining a robust security posture. - Dynamic Nature of Cloud Resources
While the ability to dynamically scale resources is a significant advantage of the cloud, it introduces its own set of security challenges. Ephemeral resources, such as auto-scaled EC2 instances or serverless functions, can be created and destroyed rapidly, making it difficult to consistently apply security controls. In a microservices architecture, where APIs are deployed as small, independent services, managing security across these numerous, fluctuating components becomes particularly complex. - Compliance and Regulatory Requirements
Many industries have specific compliance and regulatory requirements, such as GDPR, HIPAA, or PCI DSS, that dictate how data should be handled and secured. Ensuring compliance in a cloud environment requires careful consideration of data storage, transmission, and access controls. Misconfigurations or lapses in security controls can lead to non-compliance and potential legal and financial consequences.
To effectively address these challenges and secure APIs in an AWS environment, developers must adopt a multi-layered approach that encompasses best practices, advanced security measures, and continuous monitoring. In the following sections, we will dive into specific strategies and techniques to fortify your API security posture on AWS.
6 Areas of Best Practices for Securing APIs in AWS
To effectively secure APIs in an AWS environment, developers should consider implementing a number of best practices. Admittedly the list that you’re about to read is not a short one, to say the least. However, the nature and critical importance of API security means that it’s vital to have a comprehensive strategy and not cut any corners. There are 6 main areas of best practice and each one has 3 (or more) points so, with that in mind and bookmarks at the ready, let’s take a deep breath and dive in!

1. Authentication and Authorization
- Implement robust authentication mechanisms such as OAuth 2.0 and OpenID Connect using AWS Cognito to ensure only authorized users can access your APIs.
- Leverage AWS API Gateway for centralized authentication and authorization, enabling you to define and enforce access policies consistently across all your APIs.
- Utilize AWS IAM roles to grant fine-grained permissions to your API resources, adhering to the principle of least privilege.
2. Encryption
- Ensure secure data transmission by configuring your APIs to use HTTPS with TLS/SSL certificates managed by AWS Certificate Manager.
- Encrypt sensitive data at rest using AWS Key Management Service (KMS) to protect against unauthorized access.
- Store and manage API keys, secrets, and other sensitive configuration using AWS Secrets Manager, ensuring they are securely stored and easily rotated.
3. Rate Limiting and Throttling
- Implement rate limiting and throttling using AWS API Gateway
to prevent abuse, protect against DoS attacks, and ensure fair usage of your APIs.
- Define usage plans and associate them with API keys to enforce limits on the number of requests per second or per day for each client.
- Monitor API usage metrics and set up alarms using Amazon CloudWatch to detect and respond to abnormal traffic patterns.
4. Input Validation and Sanitization
- Validate and sanitize all incoming API requests to protect against common attacks such as SQL injection, cross-site scripting (XSS), and parameter tampering.
- Use AWS WAF (Web Application Firewall) to create custom rules that filter and monitor HTTP requests, blocking malicious traffic before it reaches your APIs.
- Implement strict input validation on both the client-side and server-side to ensure data integrity and prevent injection attacks.
5. Monitoring and Logging
- Enable real-time monitoring of your APIs using Amazon CloudWatch
to gain visibility into performance metrics, error rates, and usage patterns.
- Set up comprehensive logging using AWS CloudTrail to capture API calls, user activities, and configuration changes for auditing and troubleshooting purposes.
- Integrate AWS GuardDuty, a threat detection service, to continuously monitor for suspicious activities and potential security threats related to your APIs.

6. Regular Security Audits and Penetration Testing
- Conduct regular security audits using AWS Security Hub to assess the overall security posture of your API infrastructure and identify potential vulnerabilities.
- Perform periodic penetration testing, either manually or using automated tools like AWS Inspector, to proactively identify and address security weaknesses.
- Engage with the AWS security community and stay updated on the latest security best practices, patches, and advisories relevant to your API deployment.
Admittedly, that’s quite a lot to take in at first glance. However, there’s no question that these measures put you in a better position to take your API security to the next level, creating a more robust and resilient security posture in their AWS environment.
For another positive step, you could do a lot worse than to take a look at the AWS Well-Architected Framework, and specifically the Security pillar. This framework provides an expanded set of best practices and strategies for implementing a comprehensive security architecture on AWS. By following the guidelines and recommendations in the Security pillar, you can further enhance your security measures, ensuring your API and overall cloud infrastructure are well-protected against potential threats.
Security Optimisation with the AWS Well-Architected Framework
Case Studies and Real-World Examples
Securing APIs on the Holler Country website
To illustrate the practical application of best practices in API security, let's explore a real-world case study. For Spike Diamond, a Swedish digital media company, we developed a secure API management solution for their Holler Country website—a platform dedicated to country music and artist features.
This project involved setting up a comprehensive DevOps pipeline using AWS tools to ensure secure API management and deployment. The pipeline utilizes AWS CodeCommit for secure source control, AWS CodeBuild for testing, and AWS CodeDeploy for deploying API updates.
Security benefits included:
- Automated API Testing and Deployment: With AWS CodePipeline, API updates are automatically tested for vulnerabilities during each stage of the deployment process, ensuring that security standards are applied consistently.
- API Access Control: By integrating AWS Identity and Access Management (IAM), the pipeline restricts access to API configurations, allowing only authorized users to make changes and reducing the risk of unauthorized access.
- Real-Time Monitoring of API Performance: Through AWS CloudWatch, real-time monitoring of API request rates, latency, and error rates enables rapid detection and resolution of security threats or performance issues.
By automating API testing, implementing strict access controls, and utilizing real-time monitoring, this approach significantly enhances the security posture of API operations. This case showcases how AWS DevOps tools can effectively maintain secure and scalable API deployments.
AWS DevOps automates release management
Other notable examples
The ubiquity of APIs in the modern cloud environment means that successful examples of security practices are all around us, but let’s note a few high-profile instances that highlight effective API security strategies:
- Netflix: By leveraging AWS IAM roles and policies, Netflix ensures granular access control for their APIs, allowing them to scale securely while maintaining a seamless user experience.
- Airbnb: Through the use of AWS WAF and Shield, Airbnb protects their APIs from common web exploits and DDoS attacks, ensuring the safety and reliability of their platform.
- Slack: By implementing end-to-end encryption using AWS KMS and enforcing strict authentication and authorization measures, Slack safeguards sensitive user data and prevents unauthorized access to their APIs.
Together with our case study, these examples demonstrate how the effective implementation of API security best practices and advanced measures on AWS can help organizations safeguard their critical assets and maintain the trust of their customers.

Conclusion
Recap of Key Points
In this article, we have explored the importance of securing APIs in an AWS cloud environment. We discussed the unique security challenges posed by the cloud, such as the increased attack surface, the dynamic nature of cloud resources, and the need to comply with various regulations.
We then delved into best practices for securing APIs on AWS, including:
- Robust authentication and authorization using AWS Cognito and IAM roles
- Encryption of data in transit and at rest using AWS Certificate Manager and KMS
- Rate limiting and throttling with AWS API Gateway
- Input validation and sanitization using AWS WAF
- Comprehensive monitoring and logging with Amazon CloudWatch and CloudTrail
- Regular security audits and penetration testing
Furthermore, we examined advanced security measures like adopting a Zero Trust architecture, integrating security testing tools into the CI/CD pipeline, and leveraging security automation with AWS CloudFormation and Config.
API Security: An ongoing process
Securing APIs in an AWS environment is not a one-time task, but rather an ongoing process that requires continuous vigilance and adaptation. As new threats emerge and the cloud landscape evolves, it is crucial for developers to stay proactive in their approach to API security.
By implementing the best practices and advanced measures discussed in this article, organizations can significantly reduce the risk of API breaches and protect their valuable assets in the cloud. However, it is equally important to foster a culture of security within the development team, encouraging continuous learning and collaboration.
Enhance Your Cloud Security and Efficiency
Ready to enhance the security and efficiency of your cloud infrastructure? Explore our tailored AWS managed services, robust cyber security solutions, and innovative AWS Lambda offerings. Contact us today and let our certified experts guide you to a more secure and optimized cloud environment.

