Cyber Security Services
Secure your digital infrastructure with our comprehensive Cyber Security Services. CyberSec, impacting both technical and organizational domains of every process, can become complex swiftly. A structured approach like ours is vital to manage this complexity and uphold a robust security.
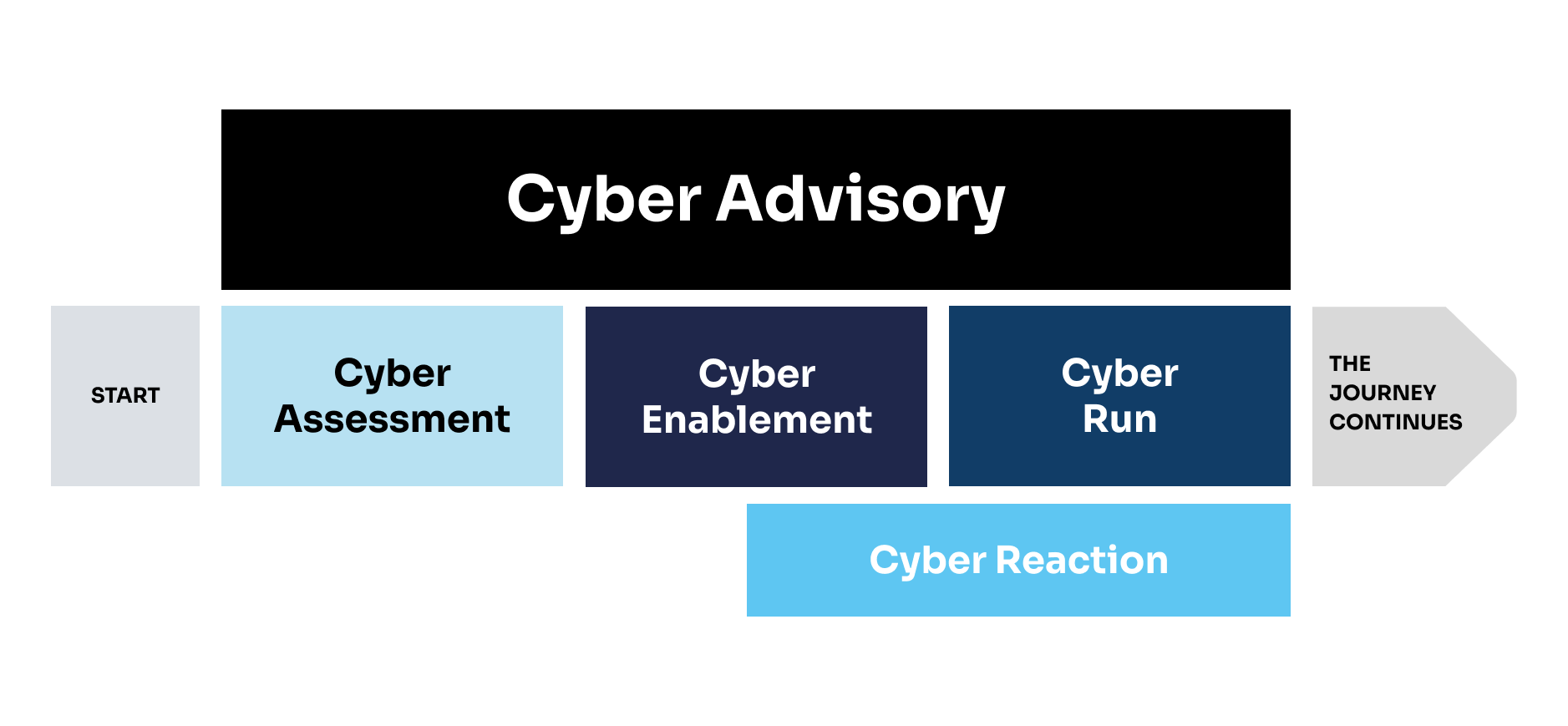
Cyber Security Assessment
Our journey begins with a Cyber Security Assessment where we evaluate existing structures and define action items based on common industry standards and best practices.
Cyber Security Enablement
Next, we provide you with bespoke or out-of-the-box solution packages through our Cyber Security Enablement service. This initiative fast-tracks your journey to a fortified digital environment.
Cyber Security Advisory
We extend our consulting services through Cyber Security Advisory. If required, our Cloud experts perform technical implementation, making us a trusted advisor enabling your organisation to make informed security decisions.
Cyber Security Run
Our SLA-based managed services, Cyber Security Run, are designed to handle the operation of cloud security tools and processes. This involves consistent monitoring to ensure seamless security operations.
Cyber Security Reaction
In the event of security incidents in the cloud environment, our Cyber Security Reaction service manages the situation and initiates effective countermeasures, automatically where applicable.
Benefits of Cyber Security Services

Complete Coverage
Our Cyber Security Services provide complete coverage, from advisory, through assessing vulnerabilities, implementing solutions and reacting to security incidents, ensuring comprehensive protection.

Efficiency and Expertise
Our Cloud Engineers employ industry best practices and standards to deliver efficient and expert solutions, enhancing your security infrastructure.

Consistent Monitoring
Through Cyber Security Run, we offer continuous monitoring of your cloud security tools and processes as part of our SLA-based managed services, guaranteeing an always-secure environment.

Trusted Advisory
We position ourselves as trusted advisors to our clients. Our Cyber Security Advisory provides necessary consulting services and optional technical implementation, enabling informed security decisions.
Cyber Security Services
Read About Our Experience With Cyber Security Services
ArticleLearn more
Mastering Cloud Security Insights, Frameworks, and Best Practices
A concise overview of cloud security, covering principles, compliance, threat detection and platform strategies, offering insights to help organizations build robust, flexible and secure practices for modern challenges.
ArticleLearn more
Do Your API Permissions Leak? A 3-Step Checkup
A 3-step guide on proactive API permission management to prevent data leaks. Covers inventorying, analysing, and automating security practices, with practical steps and recommended tools for secure cloud environments.
ArticleLearn more
Securing Serverless Applications on AWS
An in-depth guide to securing serverless applications, exploring unique risks, common pitfalls, and AWS-based best practices for identity, data, and event control.
ArticleLearn more
Advanced Security Practices for APIs in AWS Environments
A detailed guide on enhancing API security in AWS, covering Zero Trust architecture, security testing tools, and automation. Includes practical tips, best practices, and further reading for robust cloud protection.