The fifth step to a successful migration with the Microsoft Cloud Adoption Framework
The first workloads have been migrated, the technical foundation is in place – but how secure is your cloud environment really? Security in the cloud is not an afterthought add-on, but an integral part of every phase of your cloud adoption journey. In this fifth article of our series “Successful Migration & Modernization with the Microsoft Cloud Adoption Framework” we show you how to systematically secure your cloud environment.
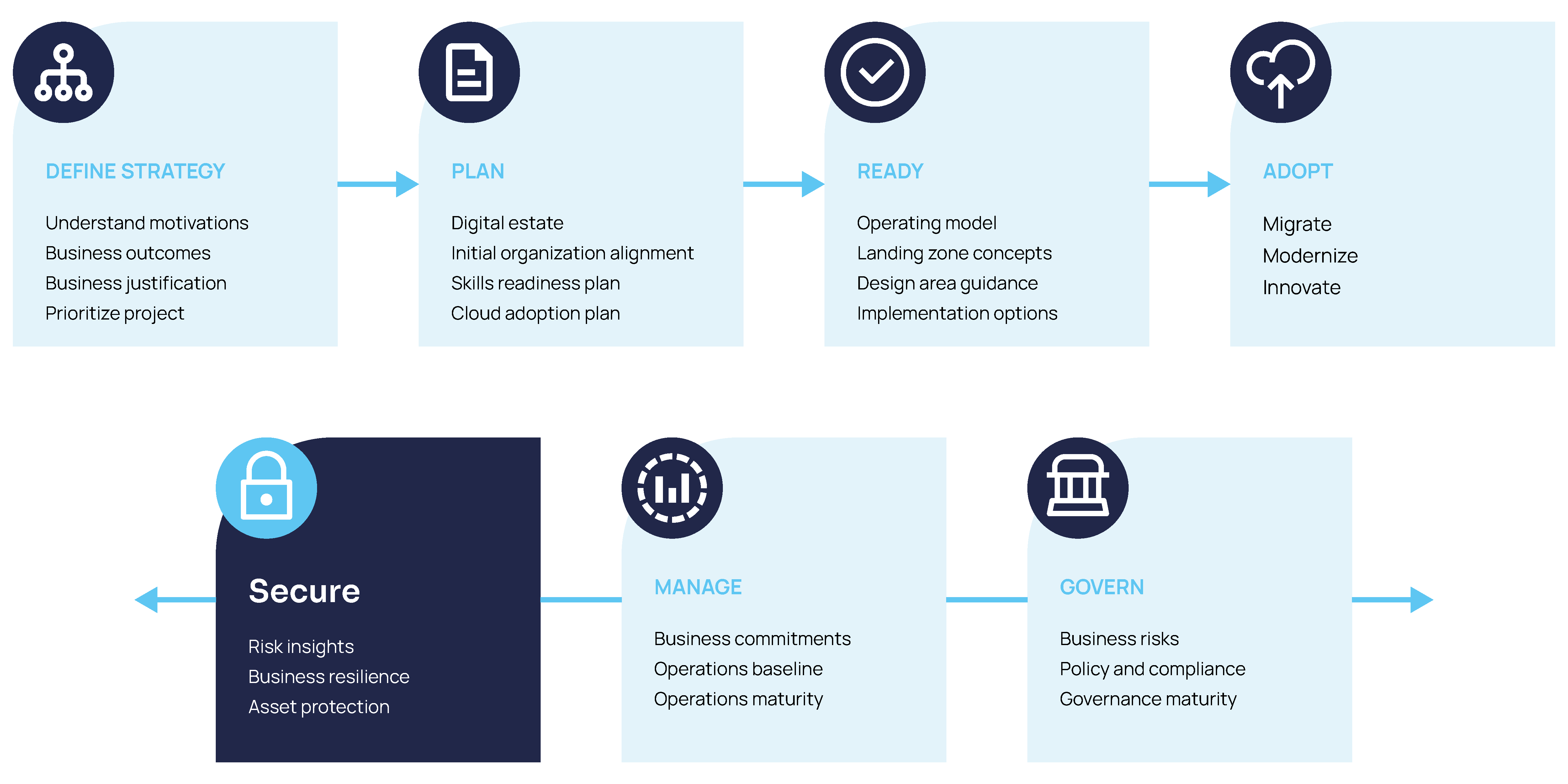
Microsoft Cloud Adoption Framework
Why Cloud Security Requires a Holistic Approach
Cloud security fundamentally differs from traditional IT security approaches. It is a complex and challenging discipline that must be considered across nearly all aspects of your cloud and technology environment. The Microsoft Cloud Adoption Framework does not treat security as an isolated phase, but as a continuous principle that runs through all methodologies.
Key Insights for Cloud Security
- Everything is a potential target: In today’s world, attackers can exploit any weakness in people, processes or technologies to achieve their goals.
- Security is teamwork: Defending against these attacks requires a coordinated approach between business, technology, and security teams. Every team must contribute and collaborate effectively.
- Shared Responsibility Model: While Microsoft Azure is responsible for the security of the cloud infrastructure, you are responsible for the security of your data, applications, and configurations within the cloud.
💡 Curious how secure your current Azure environment is? Our Azure Security Review analyzes your existing infrastructure, identifies vulnerabilities, and provides targeted recommendations to improve security and compliance.
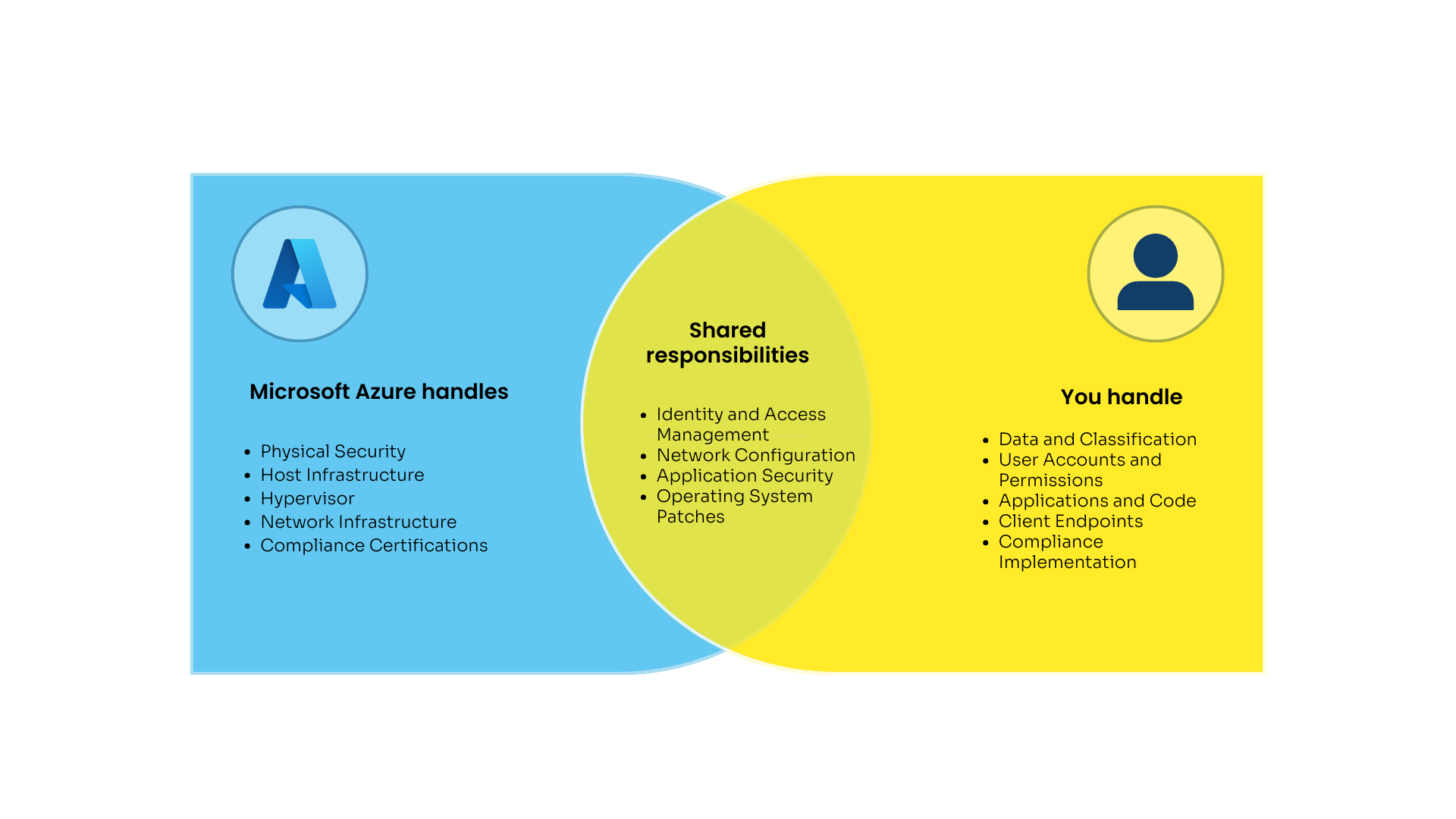
Shared Responsibility Model
Zero Trust: Trust is good, verification is better.
The Zero Trust model is based on a simple principle: “Never trust, always verify.” Instead of assuming that users and devices inside the network are secure, every access is continuously checked and validated.
The three pillars of Zero Trust
1. Identity Protection
Identities are the new perimeter. Every user and every device must be uniquely identified and authenticated.
- Multi-Factor Authentication (MFA): At least two factors for every access
- Conditional Access: Context-based access decisions based on risk, location and device
- Privileged Identity Management (PIM): Just-in-time access for admin rights
2. Device Protection
Only trusted and compliant devices can access corporate resources:
- Microsoft Intune: Device management and compliance policies
- Conditional Access for devices: Access only for registered and compliant devices
- Mobile Application Management (MAM): Protecting corporate data on mobile devices
3. Application & Data Protection
Applications and data are protected regardless of network or location:
- Azure AD Application Proxy: Secure access to on-premises apps
- Microsoft Defender for Cloud Apps: Protects cloud applications
- Azure Information Protection: Classification and protection of sensitive data
Implementing Zero Trust
Phase 1: Secure identities (MFA, Conditional Access, PIM)
Phase 2: Manage devices (Intune, Device Compliance, Endpoint Protection)
Phase 3:Protect applications and data (Cloud App Security, Information Protection, DLP)
Incident Preparation & Response
Preparing for and responding to security incidents are fundamentals of your overall security posture. Your ability to prepare for and respond to incidents can significantly influence your success in operating in the cloud.
Incident Preparation
Build a Security Operations Center (SOC):
- Microsoft Sentinel: Cloud-native SIEM for threat detection
- Azure Monitor: Comprehensive monitoring and logging
- Microsoft Defender for Cloud: Continuous security assessment
Develop Playbooks and Runbooks:
- Defined processes for different incident types
- Automated response actions
- Escalation paths and communication plans
Incident Response
Detect: Early threat detection with intelligent analytics
Assess: Quickly evaluate severity and impact
Respond: Coordinated response to contain and remediate
Learn: Continuous improvement through lessons learned
Backup, Disaster Recovery & Business Continuity
Even in the cloud, things can go wrong. A well-thought-out backup and disaster recovery strategy ensures business continuity in case of outages or attacks.
Azure Backup-Services
- Azure Backup: For VMs, files and application data
- Azure Site Recovery: For disaster recovery and business continuity
- Azure SQL Database Backup: Automated backups for databases
The 3-2-1-Rule: 3 copies of your data, 2 different locations, 1 copy offline
Disaster Recovery Planning
- Recovery Time Objective (RTO): How quickly must systems be restored?
- Recovery Point Objective (RPO): How much data loss is acceptable?
- Business Impact Analysis: Which systems are critical?
Testing is essential: Run regular restore and disaster recovery drills. Document all processes in updated runbooks.
Protecting Sensitive Data
Data protection in the cloud requires a multi-layered approach – from encryption to access control.
Encryption at all levels
- In Transit: HTTPS/TLS for all connections, VPN/ExpressRoute for secure links
- At Rest: Azure Storage Service Encryption, TDE for databases, Azure Disk Encryption
- In Use: Azure Confidential Computing, Always Encrypted for SQL databases
Key Management
Azure Key Vault for central management of keys, secrets and certificates with HSM, role-based access control and full audit logs.
Data Loss Prevention (DLP)
Microsoft Purview DLP prevents accidental sharing of sensitive data through automatic detection and policies – integrated into Microsoft 365 and Azure.
💡 Real-world check wanted? Our Penetration Testing services put your defenses to the test under real attack conditions. This way, you’ll know if your security measures really hold up.
🚀 Your Path to a Secure Cloud
Cloud security is a continuous process that runs through all phases of your cloud adoption journey. With the structured approach of the Microsoft Cloud Adoption Framework, you can build a secure, scalable and compliant cloud environment.
Your next steps:
- Conduct a security assessment: Evaluate your current security status with Microsoft Secure Score
- Develop a Zero Trust roadmap: Plan the gradual modernization of your security posture
- Build incident response capabilities: Establish processes for threat detection and response
- Implement backup & recovery strategies: Ensure business continuity
- Establish continuous improvement: Build mechanisms for long-term security
Remember: Security in the cloud is not a destination, but a journey. Every phase of your cloud adoption offers opportunities to improve and modernize your security posture.
Ready to take a systematic approach to cloud security? We’re here to support you on your path to a secure cloud:
🎙️ Practice Insights – In our „Spill IT" LinkedIn Live format , penetration testing expert Florian Wagner demonstrates how attacks really work.
📅 Coming up next week:
In the next article of our series, we’ll focus on Cloud Operations Management: how to successfully operate your cloud environment after migration, optimize costs with FinOps principles and maximize value from your cloud investment. Learn how to achieve operational excellence in the cloud.
