In the past, before the birth of the cloud, you could argue that our relationship with IT in business was much simpler. The majority of computing and data storage was done locally, often in a specific location, and anything to do with computers was largely the responsibility of the IT Department. However, in the cloud era, things are a little less clear cut. Modern organisations rely heavily on external services to store and manage data, but the rapid pace of change means that it’s still tempting to let the IT people handle everything.

While it might be tempting to defer responsibility to those with the most computer know-how, the cloud touches so many aspects of business life that you can’t escape dealing with at least some of the key principles that define our relationships with the new technologies. At the forefront of these concepts is the so-called “Cloud Shared Responsibility Model” or CSRM.
What is the Cloud Shared Responsibility Model (CSRM)?
Put in simple terms, the Cloud Shared Responsibility Model (CSRM) is a framework that defines the security roles and responsibilities between cloud service providers and customers, delineating who is accountable for securing different aspects of cloud infrastructure and data.
Each of the main hyperscalers has their own, detailed definition of the exact scope of customer and provider responsibilities. However, before delving further, it’s worth first answering the following question: Why should a business know more about it anyway?

- Legal Protection
- Cost Savings
- Reputation Management
- Strategic Advantage
- Transparent Communication
Instead of being simply a set of onerous obligations, the CSRM offers businesses a range of clear benefits. Firstly, it ensures you stay on the right side of the law by helping you comply with data protection regulations, avoiding legal headaches and often saving you money as a result. Secondly, it can also be a lifesaver for your reputation by keeping customer data safe and trust intact.
Finally, and maybe less obviously, taking CSRM seriously can also give you a strategic edge in the market by guiding smart decision-making, whilst simultaneously boosting transparency and helping you build solid relationships with customers, investors, and partners.
- PCG Managed Services: Your One-Stop Solution for Cloud Management
The CSRM in more detail
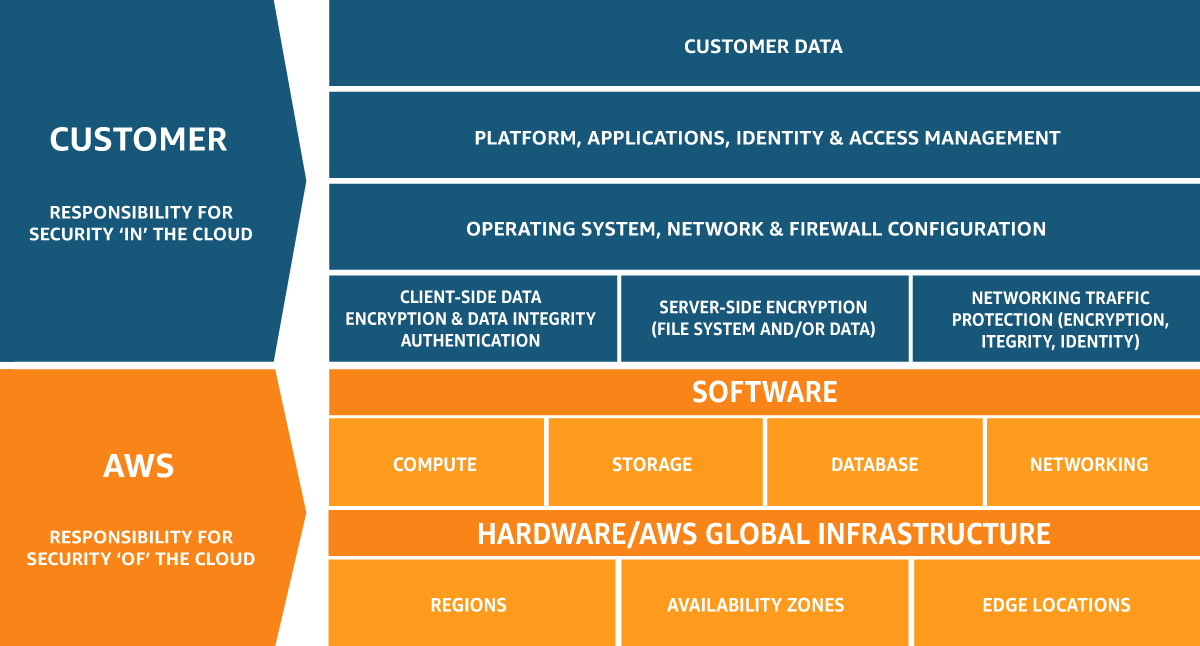
Although the Cloud Shared Responsibility Model (CSRM) touches almost every aspect of the use of cloud services, the main areas of business affected are security and compliance. The model shown above delineates the responsibilities of both Cloud Service Providers (CSPs) and customers across various layers of the cloud infrastructure, including infrastructure, platform, and software.
A key strength of the CSRM is that, at each layer, there's a clear identification of who is accountable for security measures and compliance obligations. For instance, cloud providers typically manage the security of the underlying infrastructure, while customers are responsible for making their data and applications safe.
In the next section, we will explore the specific responsibilities in greater detail to gain a deeper understanding of how each party contributes to the overall security and compliance framework of the CSRM.
- ISO 27001 - Compliance as a Service [Service]
CSP Responsibilities
Each of the major service providers’ main area of concern is to take care of the essential security and reliability aspects of the cloud. This includes keeping their data centres and network infrastructure physically secure, ensuring that your data is always available when you need it, and maintaining the overall security of the cloud infrastructure. They use various measures like surveillance systems, redundancy, and security controls to protect against threats and keep your data safe.
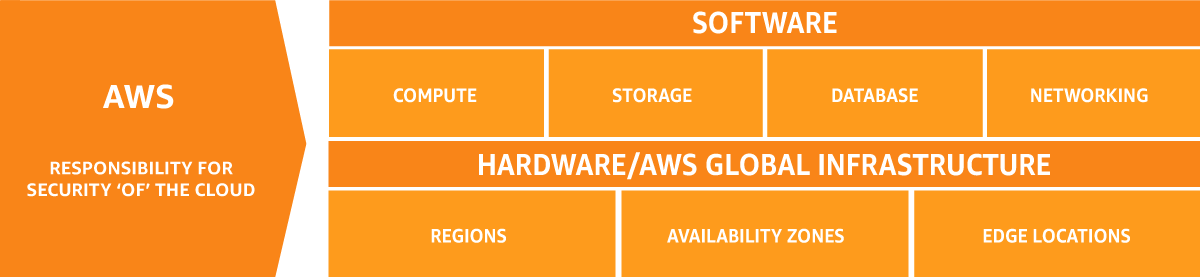
In essence, the role of the hyperscalers is to provide a secure and reliable environment for your data and applications, allowing you to focus on running your business without worrying about the technical details.
Summary of provider responsibilities:
- Physical security of data centres and network infrastructure.
- Ensuring availability and reliability of cloud services.
- Maintaining security of underlying cloud infrastructure.
Customer Responsibilities
In a similar way, customers have their own set of responsibilities, mainly to do with the actual management of data and applications within the maintained environment. These duties include tasks such as configuring access controls, encrypting sensitive data, and implementing security measures to protect against threats like malware and unauthorized access.
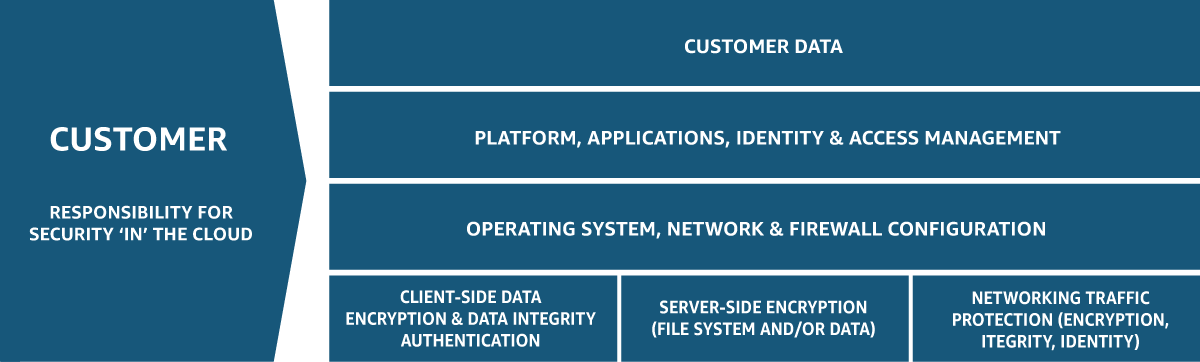
Customers are also tasked with ensuring compliance with relevant regulations and standards, as well as regularly monitoring and auditing their cloud environment for security vulnerabilities. By actively managing their data and applications, customers contribute to the overall security and integrity of the cloud ecosystem.
Summary of customer responsibilities:
- Securing data and applications within the cloud environment.
- Configuring access controls and authentication mechanisms.
- Implementing data encryption and backup strategies.
Differences between the major cloud providers
In terms of the balance of client/provider responsibilities, the major cloud services have a general consensus regarding best practices for data security, compliance, and resource management. However, nuances exist in specific areas such as data encryption standards, access control mechanisms, and compliance certifications required for certain industries. While AWS emphasizes flexibility and scalability, Azure often integrates seamlessly with Microsoft technologies, and GCP prioritizes innovative machine learning and analytics capabilities.
- See our dedicated packages for each of the hyperscalers: AWS Managed Services, Microsoft Azure Managed Services and Google Cloud Managed Services.
Challenges facing customers
Customers face several challenges within the Cloud Shared Responsibility Model (CSRM), including the complexity of understanding and managing shared responsibilities. With the division of responsibilities, it can be daunting for customers to navigate and ensure they fulfil their obligations adequately.

Additionally, there's a significant risk of misconfiguration and security breaches stemming from customer errors. Without proper expertise or oversight, customers may inadvertently misconfigure their cloud environment, leaving vulnerabilities that malicious actors could exploit.
These challenges highlight the importance of education, training, and robust security practices for customers operating within the cloud ecosystem., and can be significantly mitigated by employing two simple strategies:
- Follow a set of established best practices.
- Seek professional guidance.
Best Practices
AWS, Azure, and Google Cloud all advocate for robust security measures and compliance adherence within the CSRM and suggest several areas of best practice. These include the following recommendations that are common to all the providers:
- Access Controls & Identity Management. Implement strong access controls and emphasize identity management to regulate user permissions and restrict unauthorized access. See:
- Data Protection & Encryption. Utilize encryption techniques to protect data both in transit and at rest, and implement measures to ensure its integrity and availability.
- Monitoring. Implement comprehensive monitoring practices to detect and respond to security incidents promptly.
- Industry and Regional Standards. Adhere to compliance standards relevant to your industry and geographical region.
While the core principles align, each provider offers specific tools and solutions tailored to their platform's unique features, so it’s also important that you follow the suggested practices of your chosen cloud provider to ensure comprehensive security and compliance coverage.
- AWS: Shared Responsibility Model
- MicroAzure: Shared responsibility in the cloud
- GCP: Shared responsibilities and shared fate on Google Cloud
Still lost? Seek guidance!
These are all good tips and hopefully you now have a better understanding of the Cloud Shared Responsibility Model. However, if you’re still unsure about anything, remember that you don’t have to face the challenge alone!

As experienced cloud consultants, it’s difficult to resist pointing out the value of our insights on designing, implementing, and optimizing cloud solutions tailored to each business's specific needs and objectives. Nevertheless, the territory of security and compliance is so important to the successes of a business that it’s a false economy to try to navigate it by yourself.
By leveraging the knowledge of an experienced guide, businesses will be better placed to assess their security posture, identify vulnerabilities, and develop effective strategies to mitigate risks. Consulting with cloud professionals not only ensures informed decision-making and enhances security and compliance within cloud environments, but can also help drive success in all of your digital transformation efforts.
Elevate Your CSRM Strategy with Expert Guidance
Ready to navigate the Cloud Shared Responsibility Model with confidence? Partner with PCG, your trusted advisor in the cloud. Contact us today to learn more about how our tailored solutions can support your business in achieving its cloud security and compliance goals.
