ISO 27001 - Compliance as a Service
3 common pitfalls in getting ISO 27001 compliant
Many cloud-native companies fall into pitfalls on their way to ISO 27001 certification, which leads to unnecessary costs, time delays, and employee frustrations.
For example:
Frustrated employees: Implementing ISO 27001 mainly by employees
Most companies do not have enough resources or attractiveness to hire an experienced CISO or security specialist, as the cost for such a professional ranges between 60,000€ and 120,000€.
Often, an internal employee from the IT department is appointed to handle the ISO 27001 topic. However, these employees lack the necessary ISO 27001 knowledge and make mistakes when implementing security controls. This leads to manual processes and inefficient documentation that do not fit modern organizations like yours. The result is that the certification process is delayed by several months.
Document chaos: Hiring an ISO 27001 consultant without a tool
If you hire an ISO 27001 consultant who works without the support of tools, your employees will struggle with paper documents and Excel spreadsheets. This results in a loss of overview and transparency within the project. The ISMS implementation is not sustainable. When it comes to recertification, the time-consuming process to fill out these lists manually starts all over again.
Eliminate confusing drives, sheets, and documents to seamlessly manage your compliance work.
Inoperable software: Choosing the wrong ISO 27001 tool
Many companies try to choose and implement an ISMS tool by themselves. But how can they specify requirements for a new tool if they lack prior experience?
People often opt for the cheapest ISO tool, which may contain incorrect procedures and features. Most vendors have good marketing, but only a few provide the right features and really reduce efforts. This is why companies even migrate away from their tools when they realize the ISMS is not effective.
Using a tool doesn’t mean everything will run automatically. The software assists an expert who uses it correctly. And that is the missing piece here. Expertise is necessary for efficient project management. The best software in the world cannot replace expert guidance.
If you want to quickly and cost-effectively achieve your ISO 27001 certification, get support from industry experience and use the right ISMS tool.
Highlights
Expert Consultancy
- Our expert manages your ISMS
- We provide a clear project roadmap
- Branch-specific expert consultancy (for cloud-native companies)
- Future-oriented and sustainable
ISMS Strategy
- Creating an InfoSec strategy that fits to your business
- Understanding the business mission and aligning InfoSec smart
- Always up to date with regulatory requirements and technology
- Competitive advantage and trust
Building Up an ISMS with Automation
- One central compliance operations center
- Integration of your cloud services
- Automated evidence collection and monitoring
- Risk management and monitoring
Prebuilt policies & procedures Audit Services
- Carrying out internal audits to measure your InfoSec status
- Hand holding support during external audits
- Reducing audit workloads and preparation
- Keep your certification status pain-free
- Easily add further frameworks through cross-referencing (e.g. GDPR, NIST).


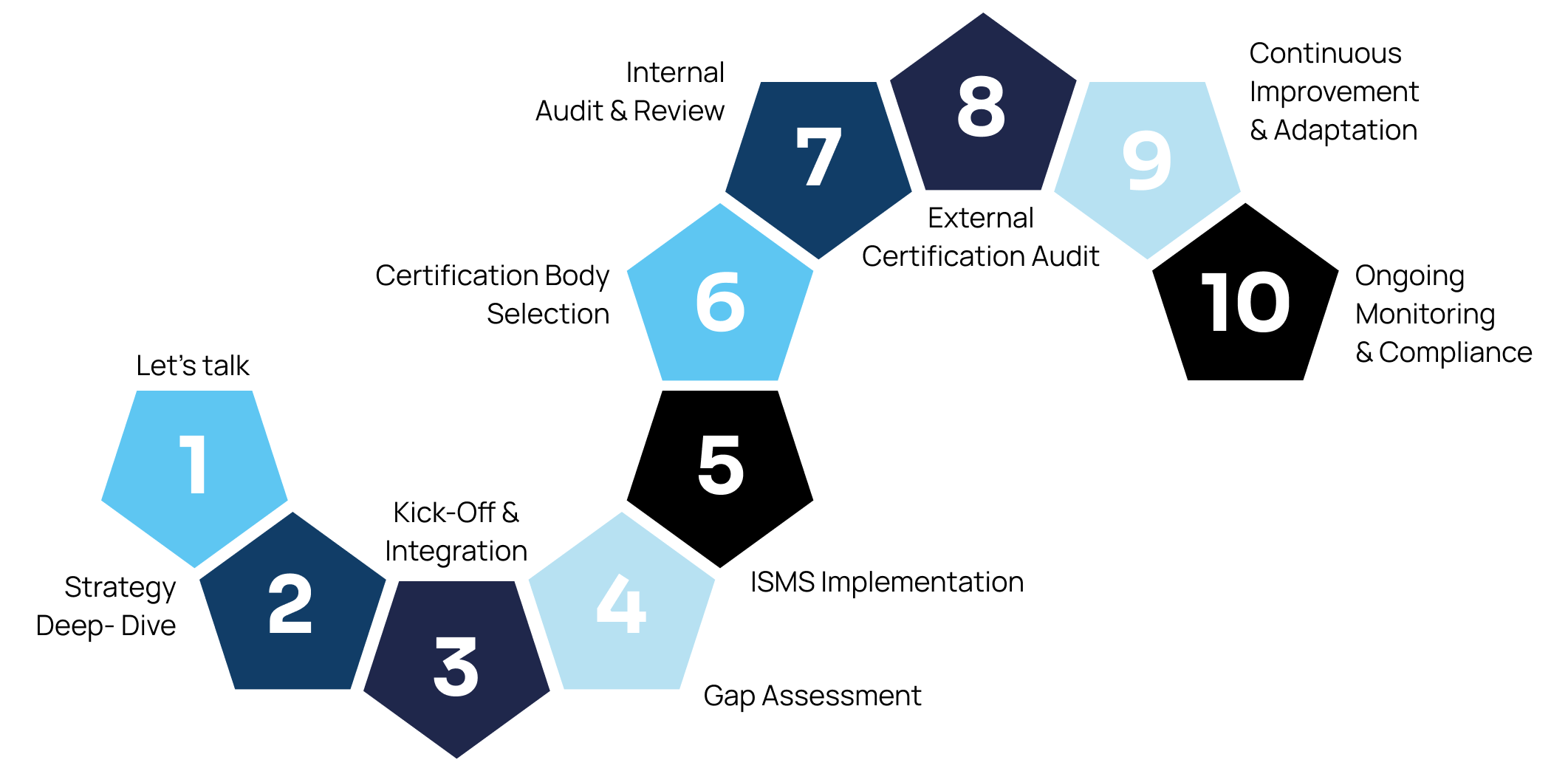
Steps of Service Delivery
Step 1: Let’s talk
Free Initial Consultation (20 mins): Understand how PCG can align with your goals during this scoping call. We'll assess your needs and set the stage for success.
Step 2: Strategy Deep-Dive
Free Strategy & Demo Session (45 mins): Discover the roadmap to ISO 27001 certification. Experience our cutting-edge ISMS service and get clarity on costs and efforts.
Step 3: Kick-Off & Integration
This phase will encompass the facilitation of initial integrations and an introduction to your designated consultant, ensuring a seamless transition into the certification process.
Step 4: Gap Assessment
We’ll conduct a comprehensive analysis of your current security protocols, identify gaps, and produce a detailed maturity report. This report will serve as the foundation for our action plan, ensuring a clear path to certification.
Step 5: ISMS Implementation
During this phase, we’ll roll out essential procedures and policies, evaluate risks, and put into place both technical and organisational controls to address identified vulnerabilities. Our audit-ready templates ensure a seamless journey.
Step 6: Certification Body Selection
We’ll assist you in identifying and selecting the most suitable certification body for your external audit, ensuring it aligns with your business needs.
Step 7: Internal Audit & Review
With our specialised toolkit, we'll evaluate the potency of your security measures, refining and readying you for the next big step.
Step 8: External Certification Audit
With our guidance, your team will be well-prepared for the external audit. We’ll provide comprehensive support throughout the process, ensuring you pass the audit on your first attempt.
Step 9: Continuous Improvement & Adaptation
Post-certification, we’ll assist in continuously refining and improving your information security practices. Whether it’s integrating organisational changes securely or incorporating new frameworks, we’ve got you covered.
Step 10: Ongoing Monitoring & Compliance
Stay ahead with our unified platform that allows for continuous monitoring of all pertinent activities. Showcase your dedication to security by sharing your compliance status with clients through a trust portal for your website.
Benefits

Industry-specific Expertise
Our professionals are specialised in cloud-based companies and managing security processes.

Efficient & Fast
Attain your ISO 27001 certification in under 6 months and pass the external audit on the first try. You save up to 70% of time and work. We are so confident in our approach, we offer a 100% pass guarantee or your money back.

Cost-effective
Opt for a smarter approach and save up to €160,000. Our centralised tools and automation outpace traditional consultancy methods in cost and effort.

Comprehensive ISMS Tool
Experience the power of our Compliance Automation ISMS Tool, designed for centralised and streamlined compliance management. Say Goodbye to Excel and Word for manual data collection, use API integrations and built in features.

Mapping of Frameworks
Map multiple frameworks in one single pane of glass and reduce checklists. Outdated information and struggles in identifying redundant security controls belong to the past.

Simplify your Audits
By sharing audit data through the platform, you reduce your audit efforts, as well as long-lasting and costly on-site audits.

Sales Accelerator
Especially for demonstrating security posture, filling out resource-blocking security questionnaires which slow down your sales, belongs to the past. You create automated trust reports and share them via your platform.

Growth & Maintenance
By outsourcing and centralising your information security, you ensure that information stays up to date. Often companies lose security maturity as consultation stops with the certification audit. We support you to improve and maintain.

Continuous Monitoring
Stay informed about your compliance with our automated checks and monitoring. Move beyond outdated reports and view your security status in real-time, anytime. Your security-conscious customers will love it.
Get started with ISO 27001 - Compliance as a Service
Read About Our Experience With ISO 27001 - Compliance as a Service
ArticleLearn more
Addressing compliance requirements with the cloud
Exploring the complexities of cloud compliance: Unveil the evolving regulatory landscape and discover how major hyperscalers like AWS, Azure, and Google Cloud simplify adherence to intricate requirements.
Press ReleaseLearn more
PCG announces change in financial leadership: Hüseyin Tastan appointed as new Chief Financial Officer (CFO)
Public Cloud Group (PCG) today announced a change in its financial leadership. After several successful years as Chief Financial Officer (CFO), Stephan Pawlowski will hand over his operational responsibilities.
Case StudyLearn more
Scaling Smarter: How StiQ Modernised on AWS with PCG
A case study detailing how StiQ modernised its digital infrastructure with PCG and AWS, achieving scalable performance, stronger security, and data-driven insight through cloud migration and integration.
ArticleLearn more
What is SAP Business Data Cloud (BDC)?
Access to a single, trusted database is crucial for making informed business decisions. SAP BTP offers a solution for precisely these use cases: the SAP Business Data Cloud (BDC).
Frequently Asked Questions
How long does it take to prepare for an ISO certification?
The time required to prepare for an ISO certification depends on various factors such as the organization’s size, complexity, existing security measures, and level of readiness. Typically, the preparation process can take several months to a year. It involves conducting a risk assessment, implementing security controls, documenting policies and procedures, and performing internal audits. With our methodology, SMEs need a maximum of 6 months cloud-native, with standard complexity and around 50 employees.
What is a Compliance Automation Platform?
A Compliance Automation Platform is a software solution that helps organizations streamline and automate their compliance processes. It enables efficient management of regulatory requirements, standards, and certifications by centralizing data, automating tasks, facilitating collaboration, and providing real-time visibility into compliance status. Additionally, all standard requirements of the respective security framework (e.g. asset management, supplier management, risk management, policies, and evidence collection) are natively provided. The manual work gets reduced by up to 70%.
What does “provision of a Compliance Automation Platform” mean?
The provision of a Compliance Automation Platform means that PCG offers a software solution to its clients that simplifies and enhances their compliance management efforts.
What is a virtual CISO?
A virtual CISO (Chief Information Security Officer) is an outsourced information security professional who provides strategic guidance and oversight of an organization’s information security practices. A virtual CISO helps you to develop and implement effective security strategies, manage risks, and ensure compliance with industry standards and regulations. The virtual CISO is especially important if you do not have know-how or resources internally.
What are the benefits of ISO 27001?
- Enhanced Information Security: ISO 27001 helps organizations improve their information security posture by implementing a systematic approach to managing risks, protecting sensitive data, and preventing security incidents. This reduces the likelihood of data breaches, unauthorized access, and disruptions to business operations.
- Increased Customer Trust: Achieving ISO 27001 certification demonstrates a commitment to information security and provides assurance to customers that their data is protected. It enhances trust, credibility, and competitiveness in the marketplace, giving organizations a competitive advantage over non-certified competitors.
- Legal and Regulatory Compliance: ISO 27001 helps organizations meet legal and regulatory requirements related to information security. By implementing the standard’s controls and best practices, businesses can ensure compliance with data protection laws, industry regulations, and contractual obligations.
- Risk Management: ISO 27001 promotes a risk-based approach to information security. It helps organizations identify and assess information security risks, implement appropriate controls to mitigate those risks, and establish processes for monitoring and reviewing the effectiveness of security measures. This proactive risk management approach reduces the likelihood and impact of security incidents.
- Improved Business Processes: ISO 27001 encourages organizations to evaluate and improve their business processes from an information security perspective. By aligning security objectives with business goals, organizations can identify inefficiencies, optimize processes, and enhance overall operational performance.
- Incident Response and Business Continuity: ISO 27001 requires organizations to develop incident response plans and business continuity strategies. This enables them to respond effectively to security incidents, minimize the impact of disruptions, and ensure the continuity of critical business operations. It enhances resilience and minimizes financial and reputational damage caused by incidents.
- Employee Awareness and Engagement: Implementing ISO 27001 involves creating a security-conscious culture within the organization. It raises employee awareness about information security risks, their responsibilities in safeguarding data, and the importance of following security policies and procedures. Engaged and well-informed employees become an integral part of an organization’s security strategy.
- Continuous Improvement: ISO 27001 promotes a culture of continual improvement in information security management. Through regular audits, reviews, and updates to security controls, organizations can adapt to evolving threats, technologies, and business requirements. This ensures that information security practices remain effective and aligned with the changing risk landscape.
Overall, ISO 27001 helps organizations establish a robust information security framework, protect sensitive information, meet compliance requirements, and gain a competitive edge in the market, while instilling confidence and trust among customers and stakeholders.
Why do startups need ISO 27001?
- Better be prepared than reactive – no matter if you are waiting for your customers or VCs to request you to prove your security status or you want to be prepared against cyber-attacks.
- A proper implementation protects you from GDPR fines (which can be up to 4% of your annual turnover).
- Data losses not only lead to contractual penalties but also implicate loss of reputation, loss of sales, or complete discontinuation of business operations.
- Easy integration – for startups an ISMS can be easily integrated into these young companies as they are more flexible in their growing phase.
- Transparency and improvement – within the ISO implementation project organizations understand that they have not been protected in the right way in the past.
- Follow a comprehensive security framework – ISO provides clear guidance and improves the maturity of security-relevant processes right from the beginning.
- Better sales – young companies have a competitive advantage compared to non-certification holders.
- Show what you got – the standard provides a simplified assurance and is used as international proof for information security.
- Clean up and enable – young companies are often less regulated, e.g. employees use different private notebooks, cloud tools of choice, and other shadow IT for business-relevant activities. The standard helps you to identify, evaluate and reduce risks without restricting the dynamics of the company.
- Get your investment – Investors take a look at the Due Diligence (and the information security strategy) of startups. ISO proactively enables and helps to fulfill these high requirements.
- Learn from the best – feedback from industry experts (e.g., auditors) allows you to discuss best practices and your current challenges.
- Save money – cost savings are measurable, e.g. for incident cases.
What happens after commissioning the ISMSaaS?
Before your official contract start, we already begin to prepare you for a smooth launch. This includes scheduling your project kick-off at an early stage. You will receive more detailed information from us about 10 days before the start of the contract. Here you will also find further details on the project process and the first important steps. The platform access is created with the start of the contract.
What means cloud native?
A cloud-native company embraces the cloud as a core part of its business model, leveraging its advantages to deliver scalable, resilient, and efficient applications and services. That means you do not operate your own data center (servers and storage). Our services work through fetching information from the API endpoints of hyperscalers (e.g. AWS, Azure, GCP) and other SaaS platforms, to automatically check and monitor the configuration.
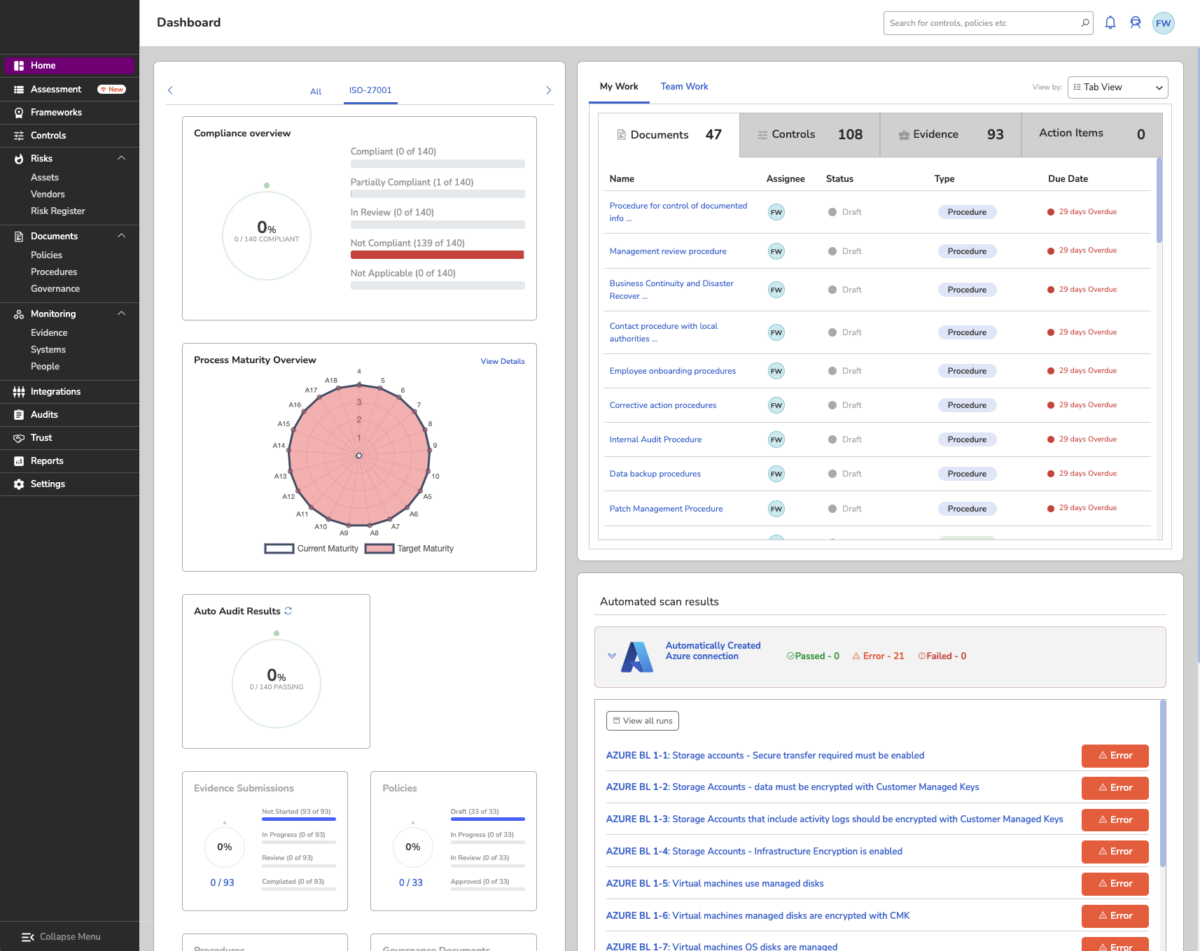
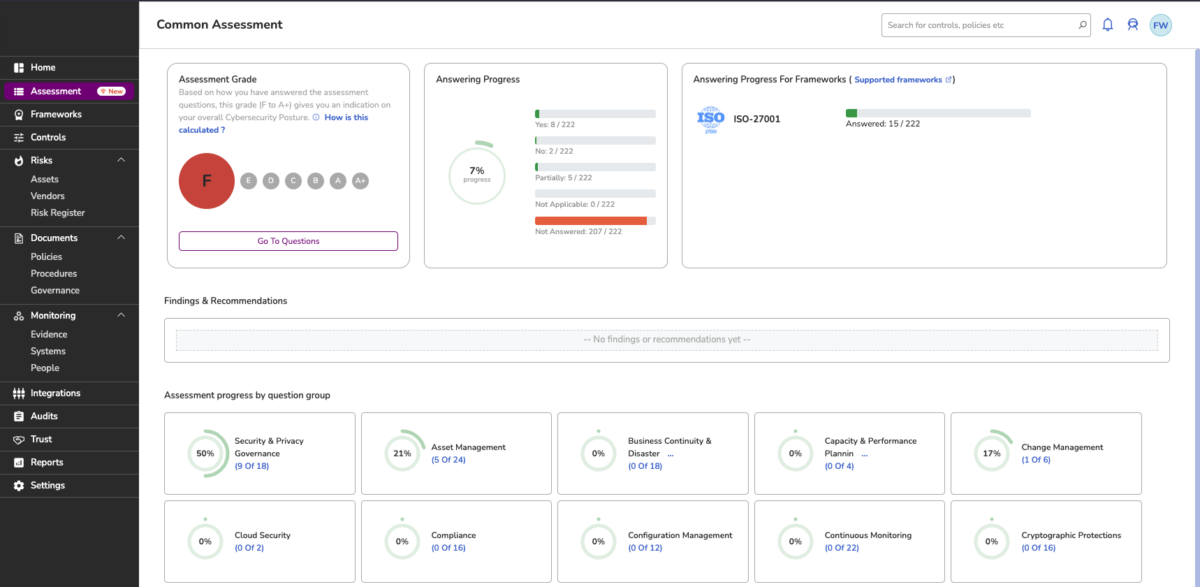
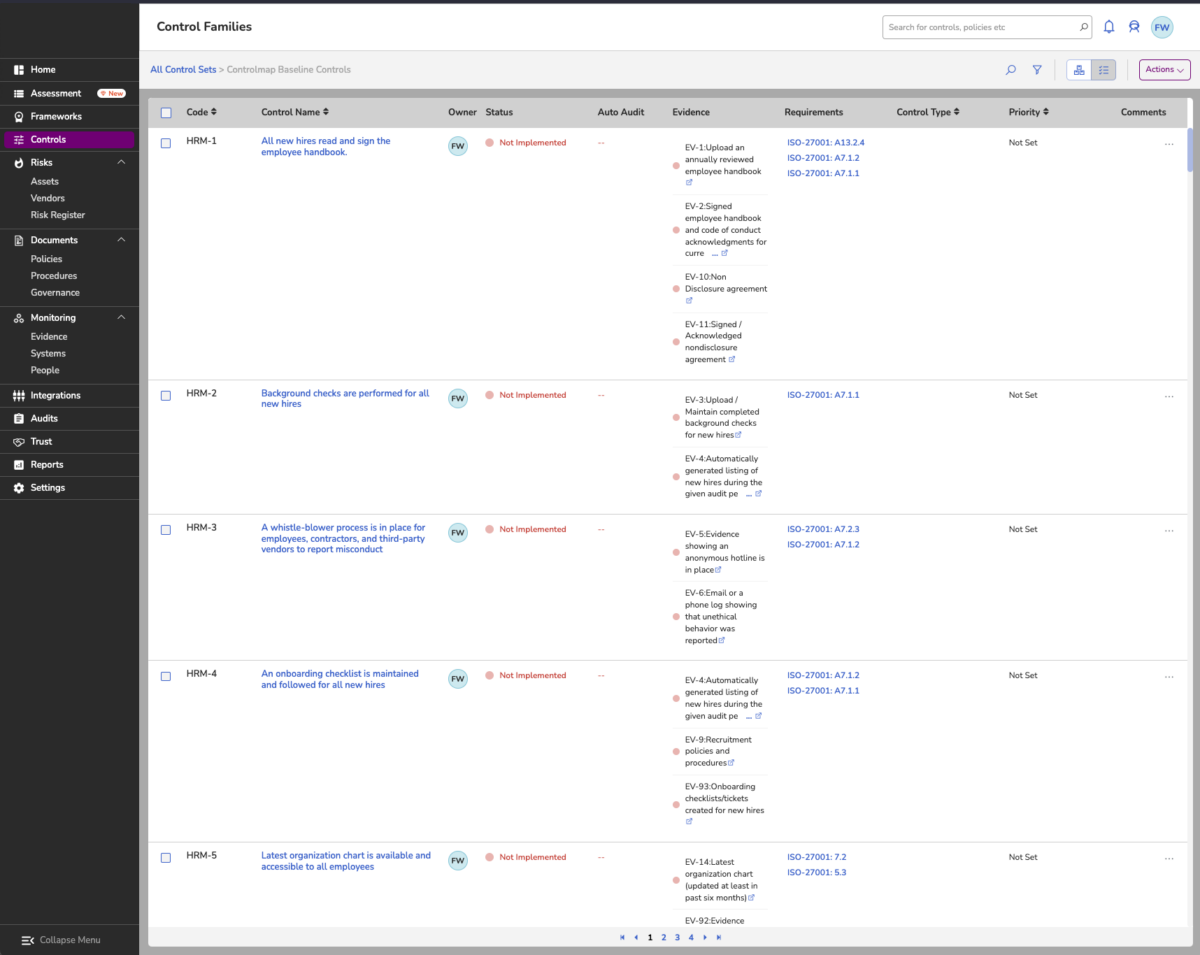
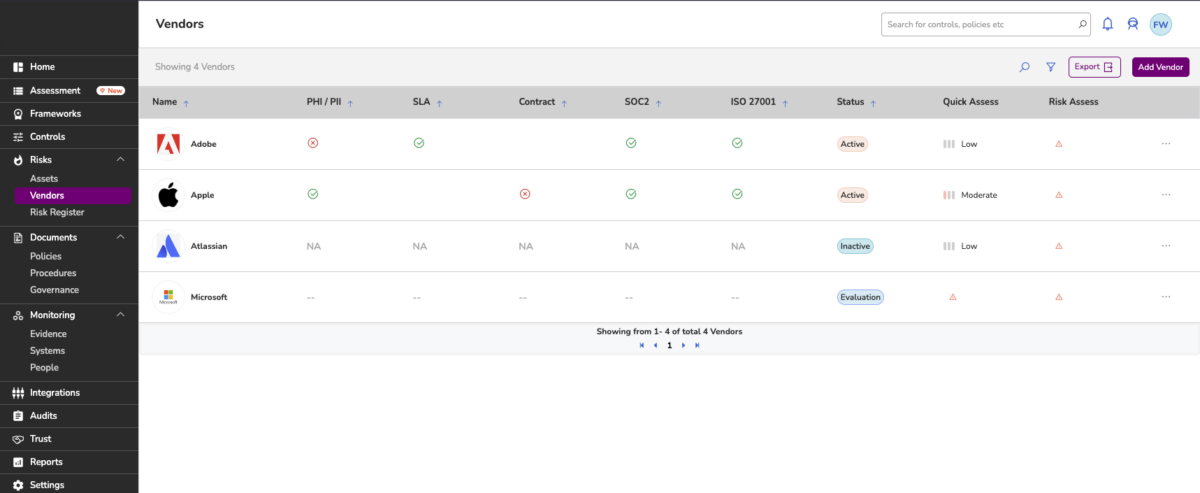
How does the Compliance Automation Tool look?
1. Dashboard
2. Assessment
3. Frameworks

4. Controls
5. Vendor Management
6. Risk Management
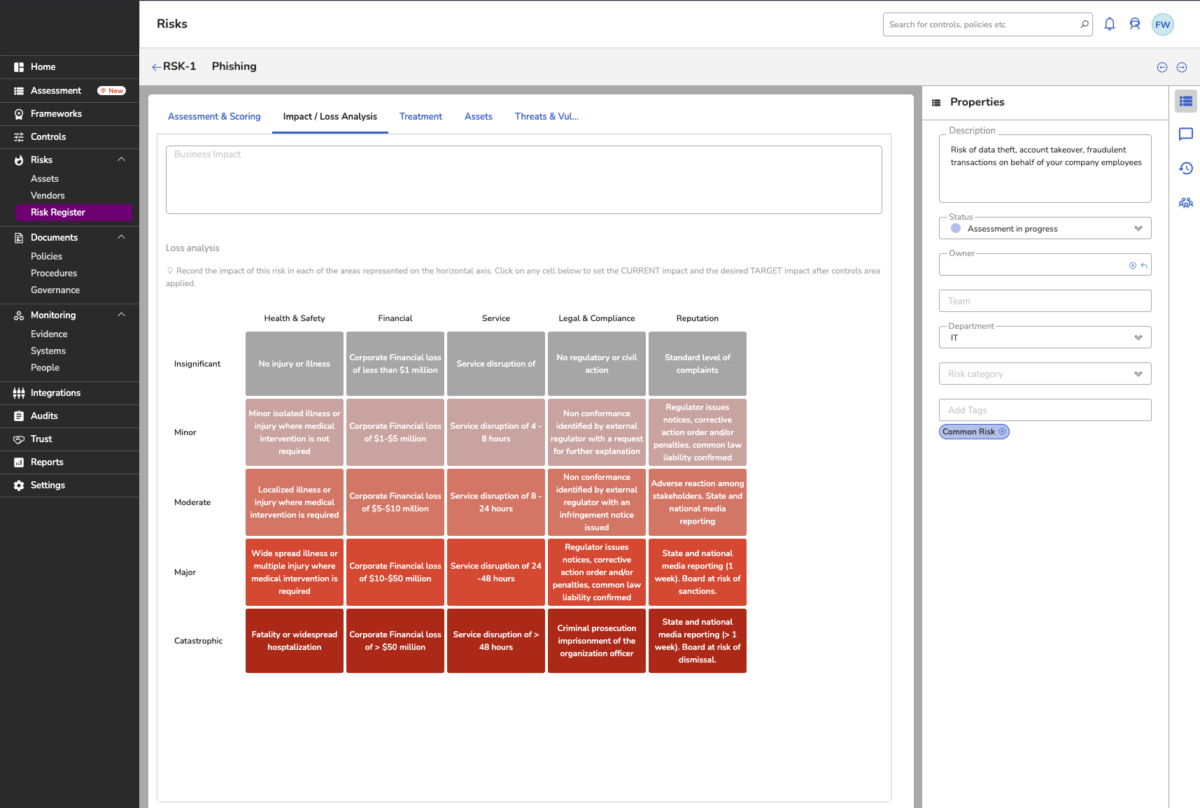
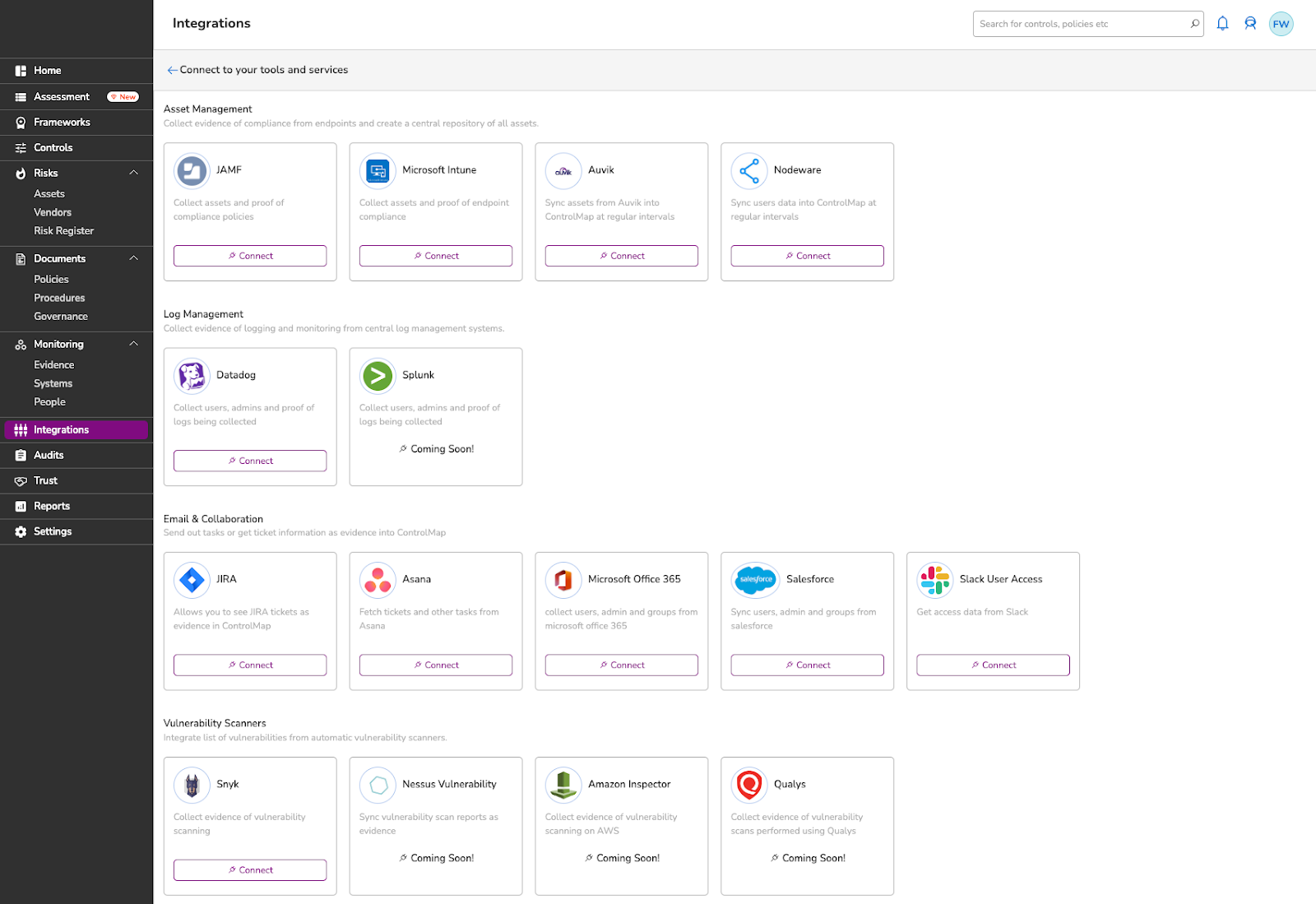
7. Integrations

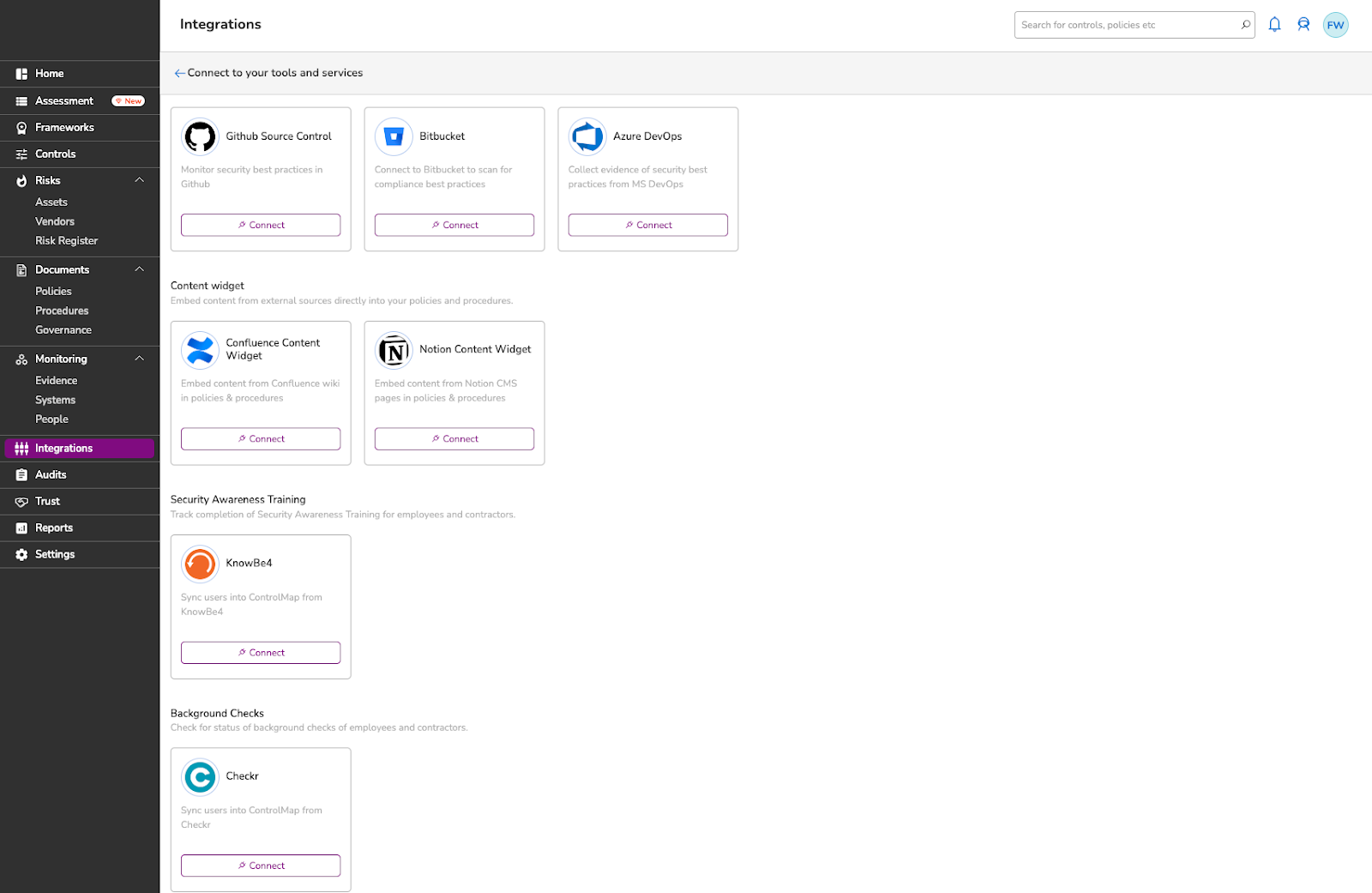
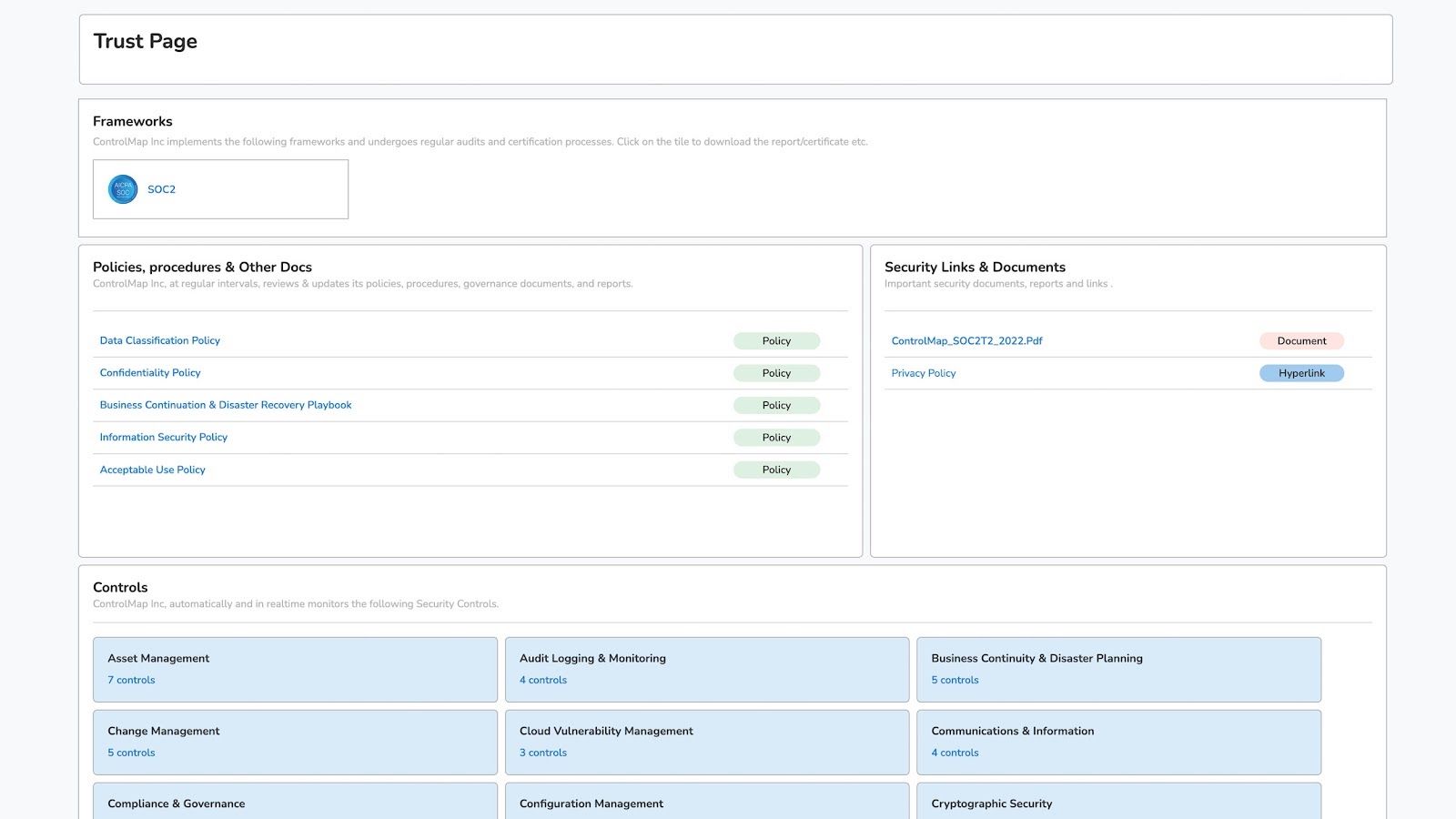
8. Trustpage
What frameworks do you support?
PCG provides the tools and resources necessary to comply with 35+ in-demand security frameworks. Now, you can easily show your commitment to cybersecurity, reduce your sales cycle time, and expedite your compliance journey.
Supported Compliance Standards:
- SOC 2 Type 1 & 2
- ISO 27001
- NIST CSF
- CMMC
- CSA CCM
- COBIT 2019
- HIPAA
- GDPR
- FedRAMP
- CCPA
- CIS Controls
- PCI DSS
- MARS
- TX-RAMP
- ISO/IEC 27018:2019
- SCF
- ISO 27701
- Microsoft DPR
- TISAX
- UK ICO
and many more.