Getting a complete overview of all existing and newly created resources, analyzing their security posture in real time and acting timely or even automated is vastly simplified using the Datadog resource inventory feature.
Problem
In the rapidly evolving landscape of cloud computing, organizations face several common challenges when it comes to managing their AWS (Amazon Web Services) resource inventory. Many organizations grapple with the limited visibility of their AWS resources, facing challenges due to the fragmented nature of their infrastructure. The absence of a consolidated user interface (UI) for resource inventory hampers efficient access to vital information. Resource tracking, involving categorization by type, region, and account, becomes a cumbersome task, contributing to inefficiencies in resource management and oversight. Additionally, organizations often lack an accessible mechanism to view key configuration attributes for each resource, impeding effective monitoring and management. Initial resource discovery within the AWS environment poses a challenge, requiring the implementation of mechanisms such as AWS describe APIs for accurate inventory building. Furthermore, the task of keeping the resource inventory up to date is a continual challenge, necessitating prompt identification of new resources, updates, or terminated resources for real-time updates.
Solution
To address the common challenges faced by organizations, Datadog’s Cloud Security Management provides a comprehensive solution with the following capabilities. First and foremost, it offers a consolidated user interface (UI) that efficiently displays AWS resource inventory information. This UI allows users to access and organize data by resource type, region, and account, providing a centralized platform to view critical configuration attributes. Additionally, the solution tackles the challenge of resource discovery by leveraging AWS describe APIs, facilitating an initial exploration of resources within the customer’s AWS environment and populating the resource inventory. To maintain an up-to-date inventory, Datadog’s solution utilizes an event-driven framework. This framework continuously monitors and identifies new, updated, or terminated resources, ensuring prompt updates to the resource inventory for effective and real-time management.
The Result
By implementing integration between Datadog and AWS and enabling Datadog Cloud Security Management, organizations can achieve the following outcomes:
1. Efficient Resource Management
The consolidated UI allows organizations to access and manage AWS resources more efficiently. They can view inventory information based on resource type, region, and account in one place.

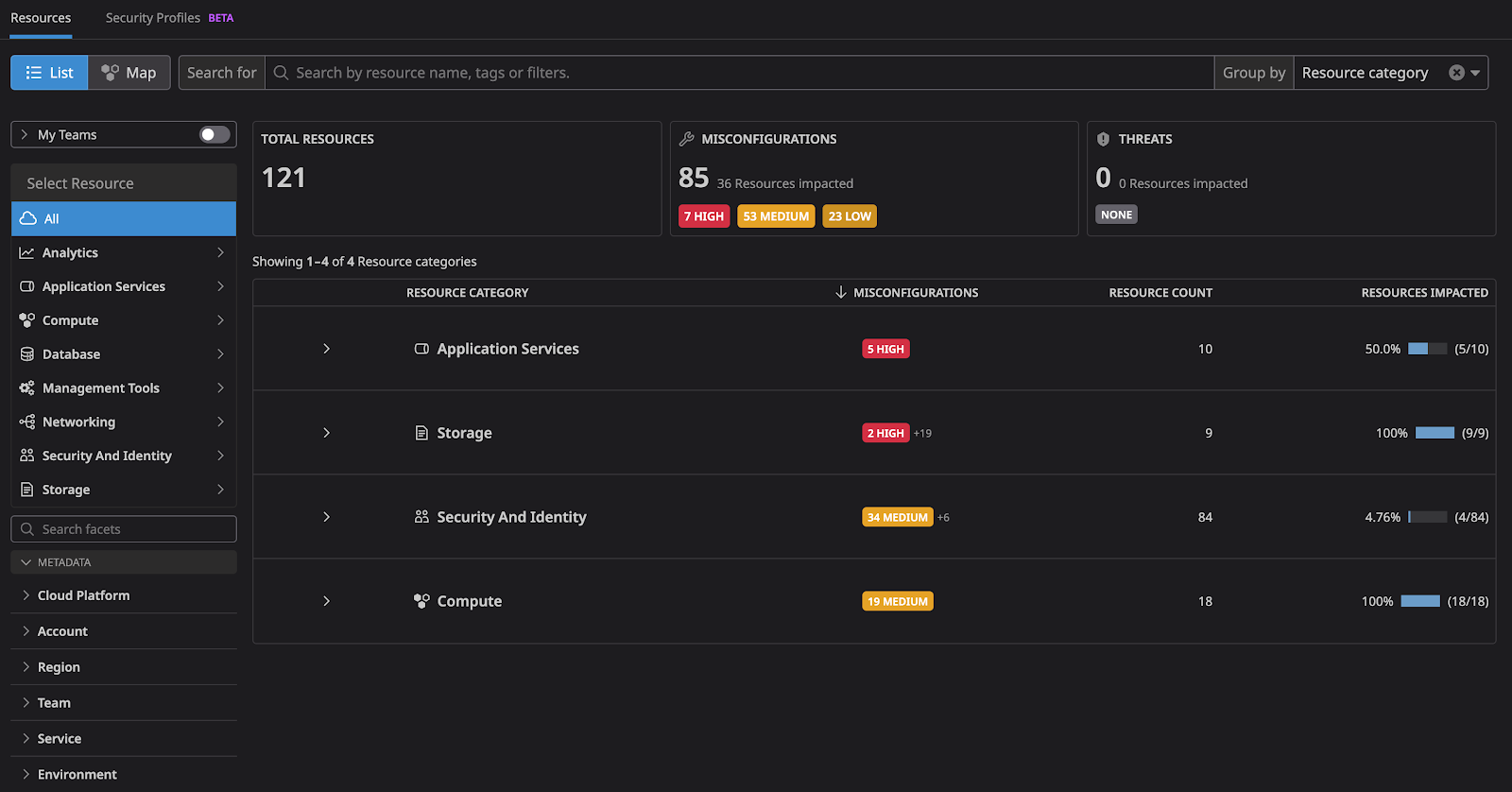
2. Resource Visibility
Users can readily access key configuration attributes and tags for each resource, which enhances resource visibility and aids in effective monitoring and management.
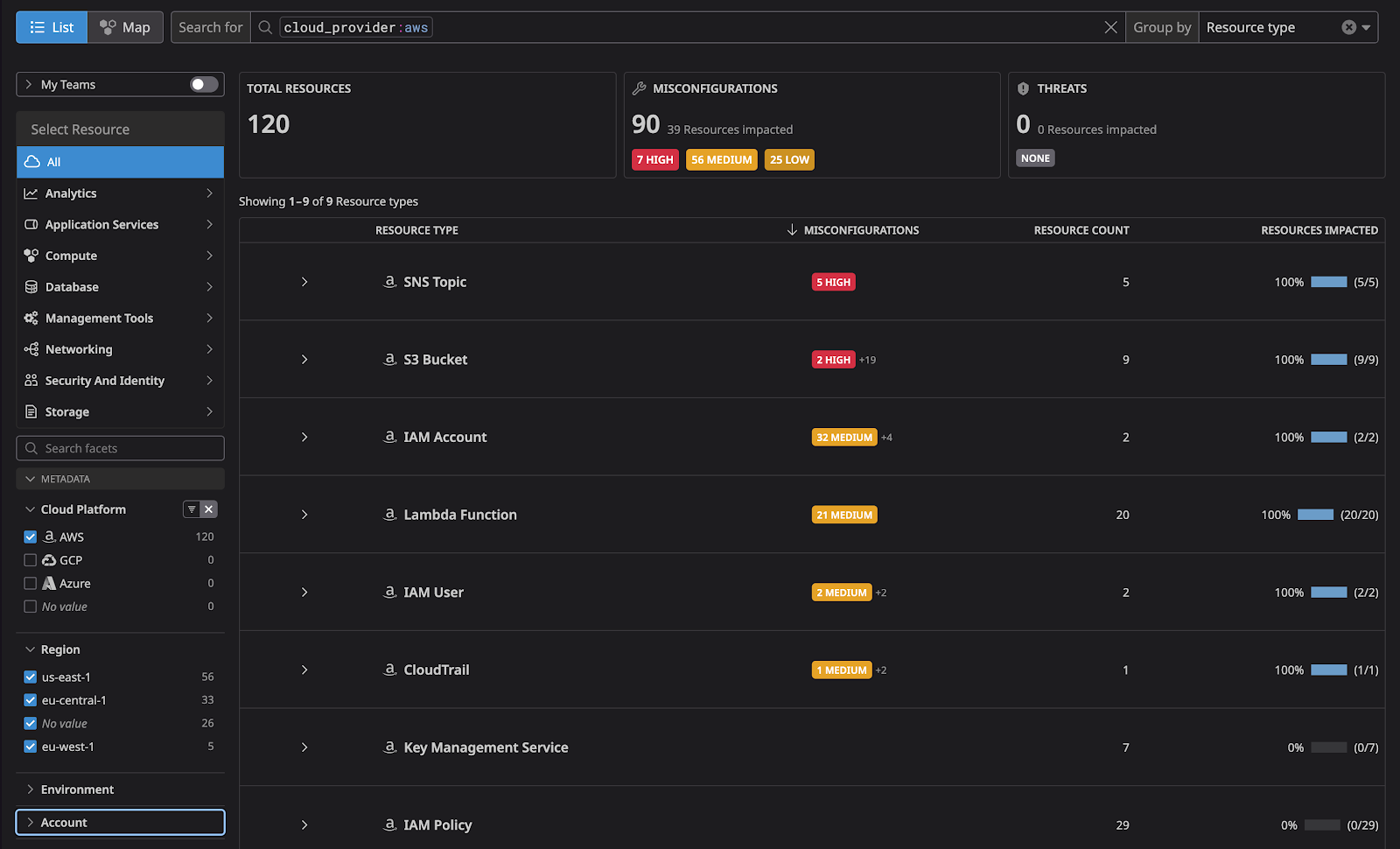
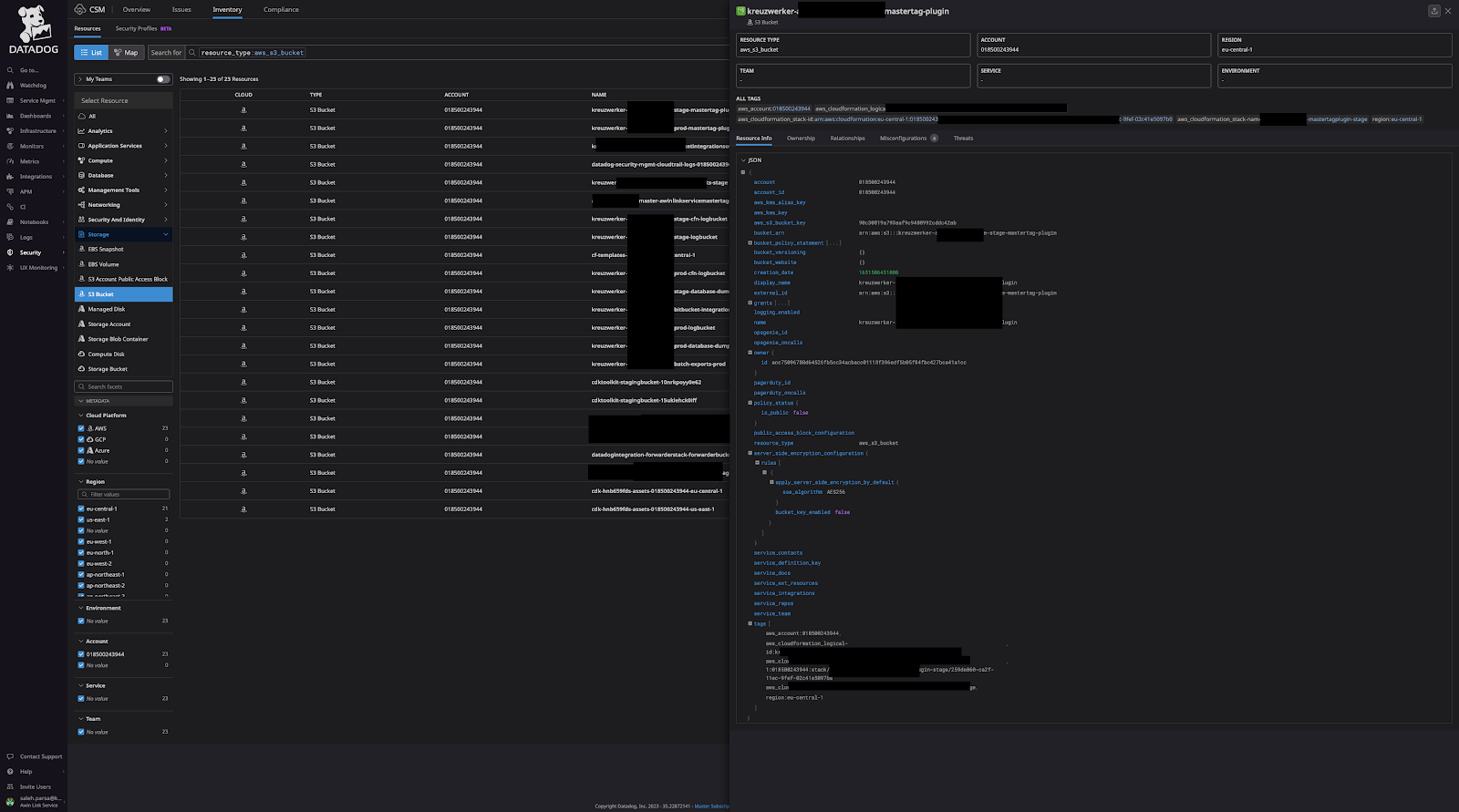
3. Resource Discovery
The solution’s initial resource discovery capability ensures that the inventory begins with an accurate representation of AWS resources.
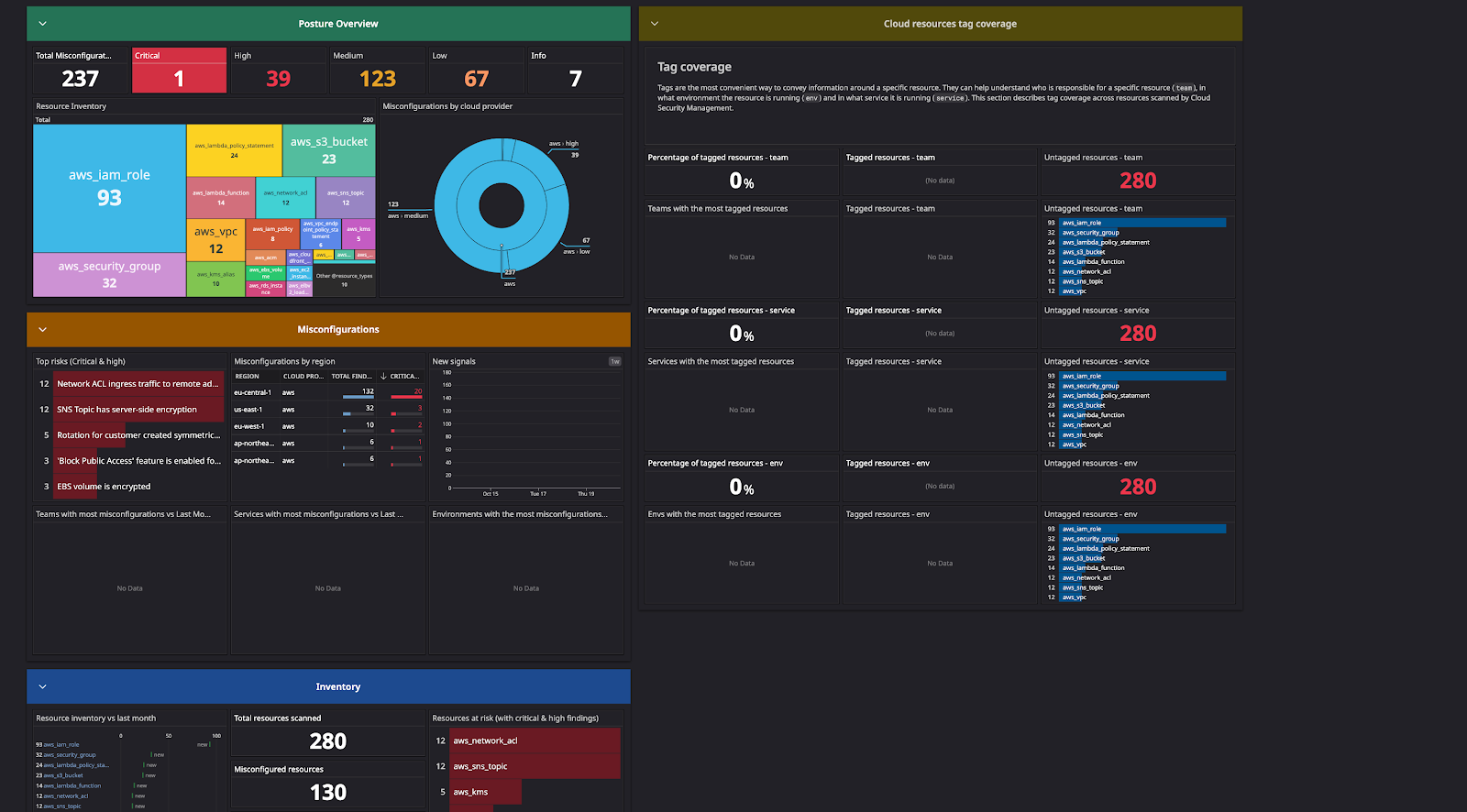
4. Real-time Updates
The event-driven framework ensures that the inventory remains up to date by identifying and reflecting changes to resources in a timely manner.
Conclusion
In conclusion, this case study highlights the value of using Datadog Cloud Security Management that addresses common challenges in AWS resource inventory management. By providing a consolidated UI, resource discovery through AWS APIs, and real-time updates, organizations can efficiently manage their AWS resources and enhance visibility, ultimately leading to better resource governance and control.