This article covers:
- Description and details of the AWS ECR image scan feature
- Outline and details of an automated usage proposal
- The single parts of the proposed approach shown in detail
The AWS feature
AWS Elastic Container Registry has been able to support the scanning of images for vulnerabilities using the open source project Clair for quite some time now. Clair is an open source project used for the static analysis of vulnerabilities in application containers (currently including OCI and Docker). Made available by AWS directly and implemented into ECR, it is a very useful feature to minimize the risk of using endangered software - and stay compliant. The scanning for vulnerabilities should be a good standard in any Dockerized scenario as public images and their heirs can contain many security risks (Top-ten-docker-images
) - which might be overlooked while developing applications that are constantly changed and improved - and new versions of images are pushed to your ECR many times a day.
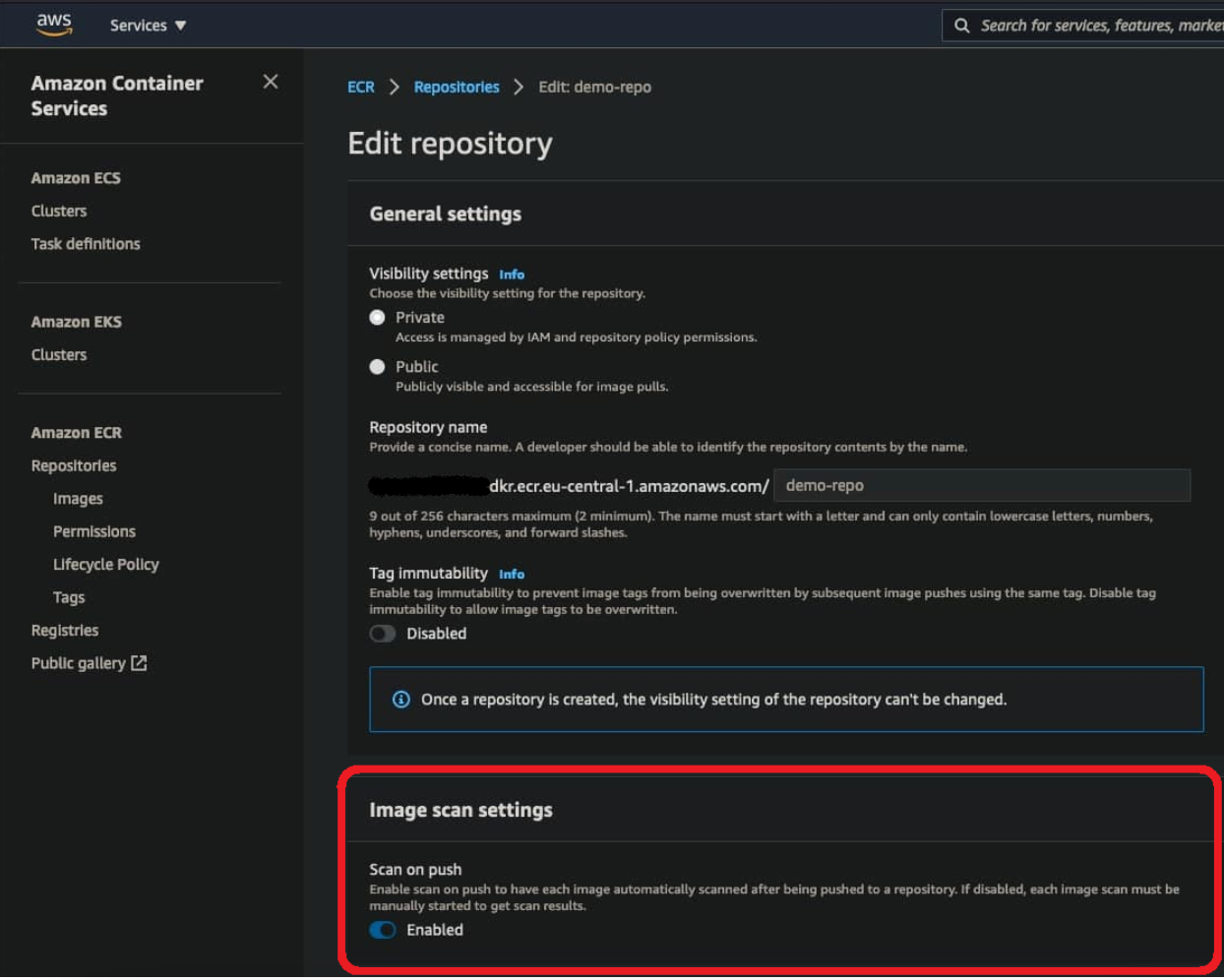
AWS ECR supports automatically scanning any pushed image per repository or to trigger a scan manually - which can be configured any time in the settings of an individual repository:
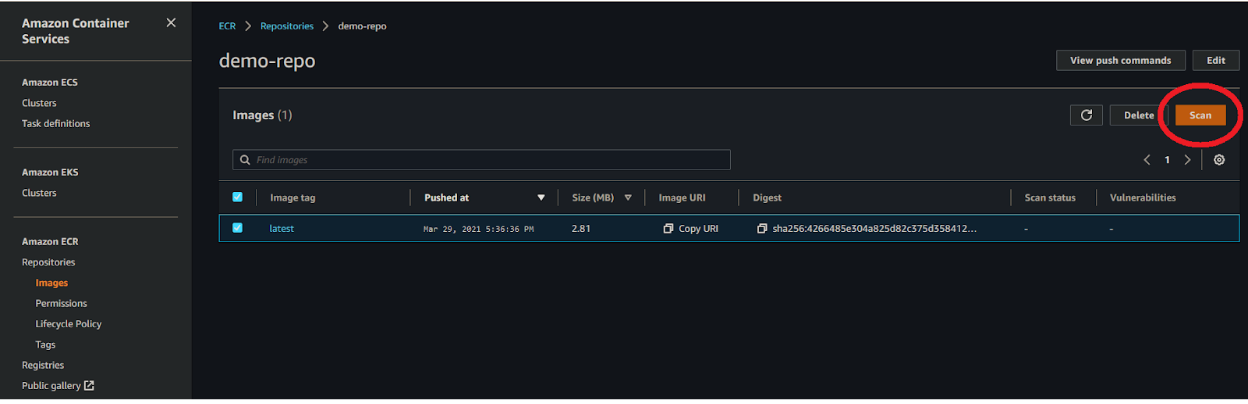
Scanning and the list of results can accessed via the management console:
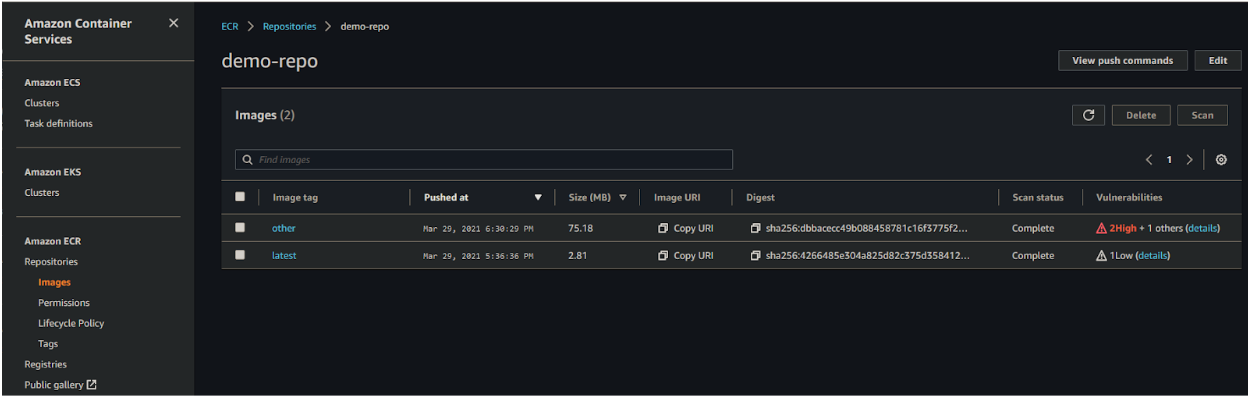
Findings are shown in the overview with a short summary:
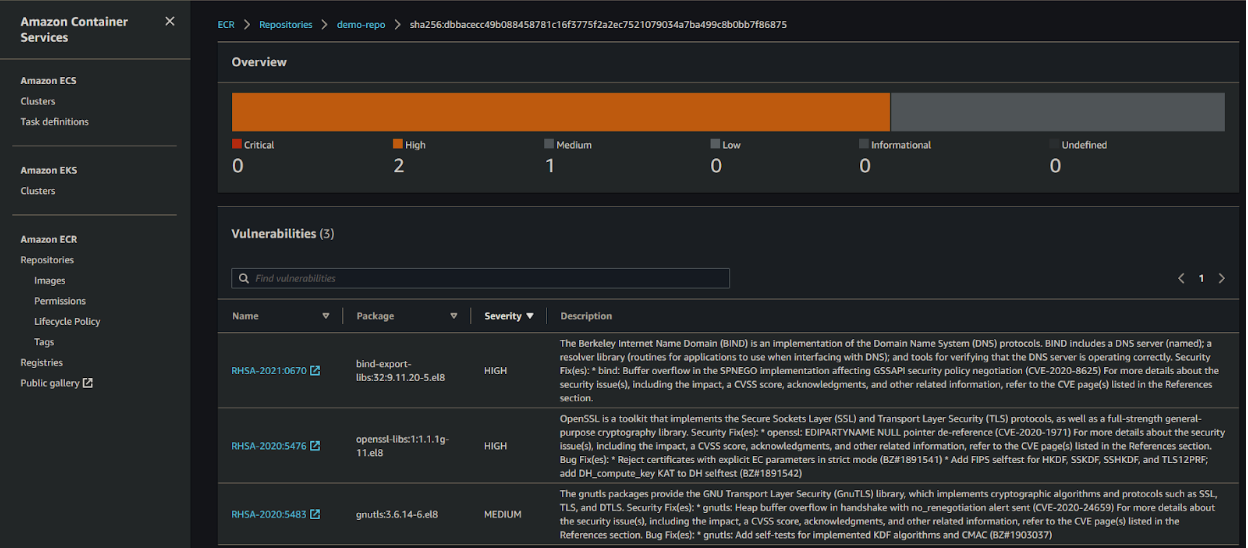
Details explain exactly what threat or risk was found:
For more details about the feature, please see the documentation.
So much for the manual usage of the feature. Nobody really wants to scan and check in the console every time a new container is built and pushed 😃
Using the automated image scanning in AWS ECR is a good start to automate, but if nobody looks into it, it doesn’t help much. Getting notified with the results automatically will greatly enhance your awareness for security risks that could be implemented in your application by using insecure images.
Outline and details of the proposed solution
The quick description:
- Enable “scan on push” - for all repositories in your AWS account (manually enabling is shown in the section above).
- This will trigger an image scan, each time an image is pushed to one of your repositories.
- An event of the type “ECR Image Scan” is published to the AWS event bridge when the scan is finished. The event details contain data about the image and number of findings
- Define an event rule that transforms the data from the event to readable data and forwards it to an SNS topic
- From the SNS the next target
The data of a typical event used in this example looks like this:
The tiny parts:
For demonstration of the parts needed and the deployment, terraform was used, resources step by step:
1. ECR Repository with “scan on push” enabled:
2. An AWS Event Bridge rule (formerly Cloudwatch rule, in terraform still Cloudwatch) to receive and handle events:
3. A target for the event rule… an SNS topic:
4. A SNS subscription which forwards to lambda:
5. The target lambda function:
The lambda function itself is a simple Python script, posting the message in the correct format to the HTTP webhook of the Slack channel:
The sample code can be found here, please feel free to use.
Conclusion
A notification in Slack could look like this:
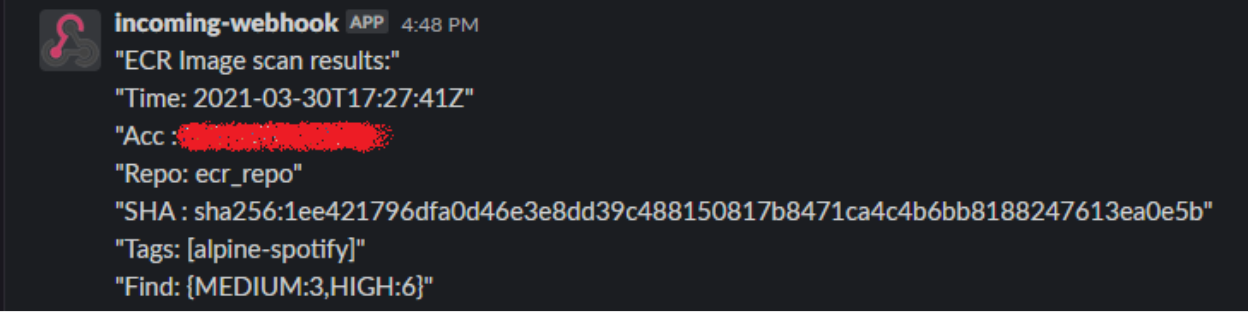
It contains all information needed to act upon - the details of the security risks found in the image can be retrieved from the console (as shown earlier in the article).
The approach shown here is easy to use, easy to implement, easy to to adapt to more options - and definitely worth the while to enhance security for any containerized solution running on AWS.