Cyber Security Consulting
Enhance your organisation's cybersecurity posture with our comprehensive Security Consulting services, including tailored implementations of Zero Trust, IT-service Continuity Strategy (ITSC), Identity Management Strategy, and Crypto Strategy.
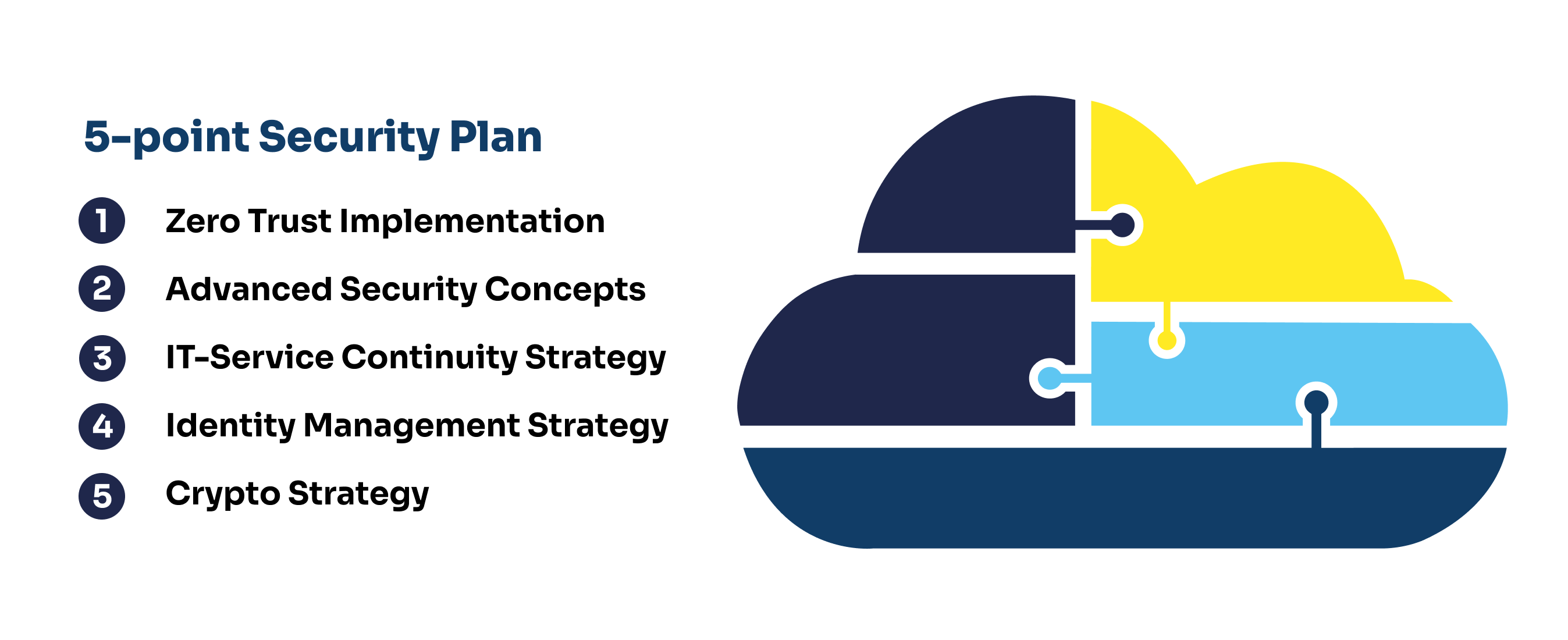
Advanced Cyber Security Concepts
With our cyber security consulting services, your company can effectively navigate the dynamic landscape of cyber environments, technologies, best practices, and the threat environment. Our guidance spans from Zero Trust and Workload Separation to BYOB / HYOK and Advanced Threat Prevention.
Zero Trust Implementation
We help demystify the buzz around Zero Trust. Our expert team provides insights, strategic planning, and ongoing guidance for implementation. A correctly executed Zero Trust concept reduces risks, enhances usability, and boosts system acceptance.
IT-Service Continuity Strategy (ITSC)
We assist in establishing robust IT-processes that withstand crisis events, covering redundancy measures, scenario-based contingency planning, and regular testing of these protocols.
Identity Management Strategy
Our team helps implement an effective, highly automated authorisation and authentication process that includes not just your internal employees but also services, applications, and third parties.
Crypto Strategy
Work with us to tackle encryption at multiple levels, considering what needs to be encrypted and how. These are paramount considerations in cloud environments.
Benefits of Cyber Security Consulting

Comprehensive Approach
Our holistic approach to cybersecurity addresses everything from Zero Trust implementation to IT-service Continuity Strategy, Identity Management, and Crypto Strategy.

Tailored Strategies
Strategies are customised to your specific needs, covering a variety of environments including AWS, Google, and Microsoft.

Discovery Workshops
Through our workshops, we help you identify use cases and guide you towards the implementation of the most practical and cost-effective solutions.

On-Going Support
Whether you need a trusted advisor for occasional consultations or a managed service for a more hands-on approach, we've got you covered.
Get started with Cyber Security Consulting
Read About Our Experience With Cyber Security Consulting
ArticleLearn more
Mastering Cloud Security Insights, Frameworks, and Best Practices
A concise overview of cloud security, covering principles, compliance, threat detection and platform strategies, offering insights to help organizations build robust, flexible and secure practices for modern challenges.
ArticleLearn more
Advanced Security Practices for APIs in AWS Environments
A detailed guide on enhancing API security in AWS, covering Zero Trust architecture, security testing tools, and automation. Includes practical tips, best practices, and further reading for robust cloud protection.
Case StudyLearn more
New paths in IT: AGRAVIS embraces Cloud innovations
AGRAVIS Raiffeisen AG, a leading agricultural trading company in Germany, faces the ongoing challenge of adapting its IT infrastructure to the constantly changing demands of agriculture.
ArticleLearn more
Benefits of Managed Service Providers in the Cloud
Discover the valuable benefits of having a Managed Service Provider in the Cloud, and how you can increase value and eliminate worry.