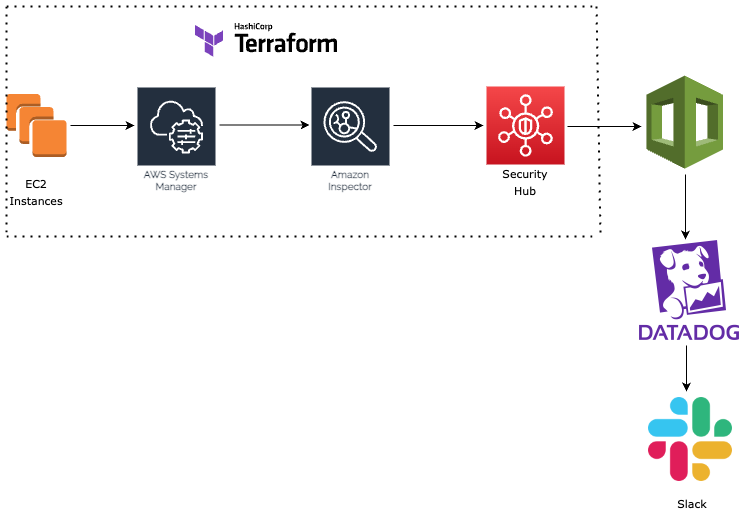
Many companies are affected by availability and security vulnerability issues regarding their applications and infrastructure. This blog describes how we at PCG combine scanning, monitoring and communication tools to identify and mitigate security findings in order to avoid exploits, compromised systems and unintended network exposure, which could potentially cause extensive financial and business damage to our customers.
Problem
During a well-architected framework review (WAFR), different severity findings were identified, prompting the customer to reach out to us to shape their security journey. Security is now more essential than ever. During the last few years, the trend of global attacks has increased exponentially, causing huge costs for the affected companies.
Our approach
Our first step was to combine Amazon Inspector and Security Hub in order to provide a stable and continuous vulnerability scanning solution. In the second stage, we designed the notification workflows to send warning and critical alerts respectively to our Slack channel and monitoring platform, Datadog. This ensures centralized monitoring of all infrastructure components, efficient analyses, quick reaction and mitigation.
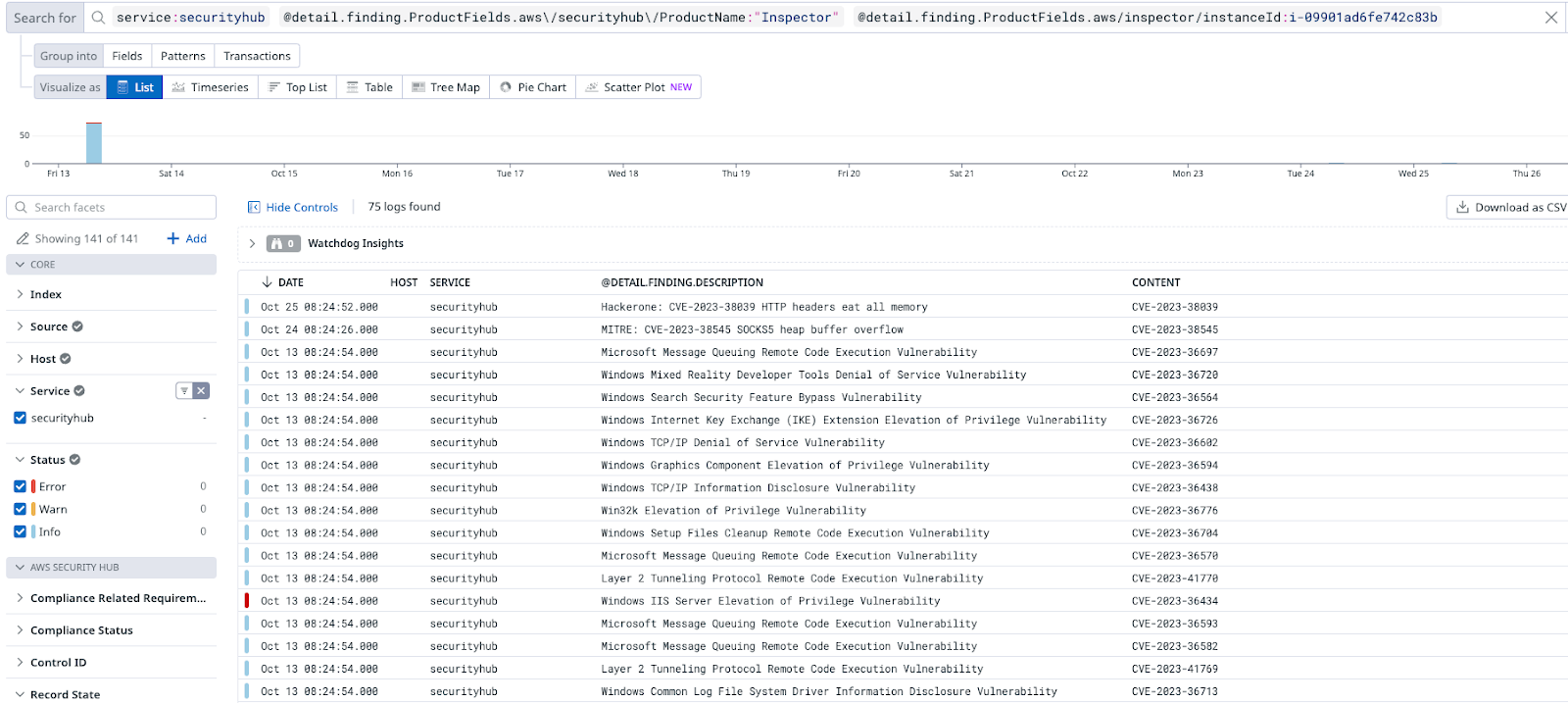
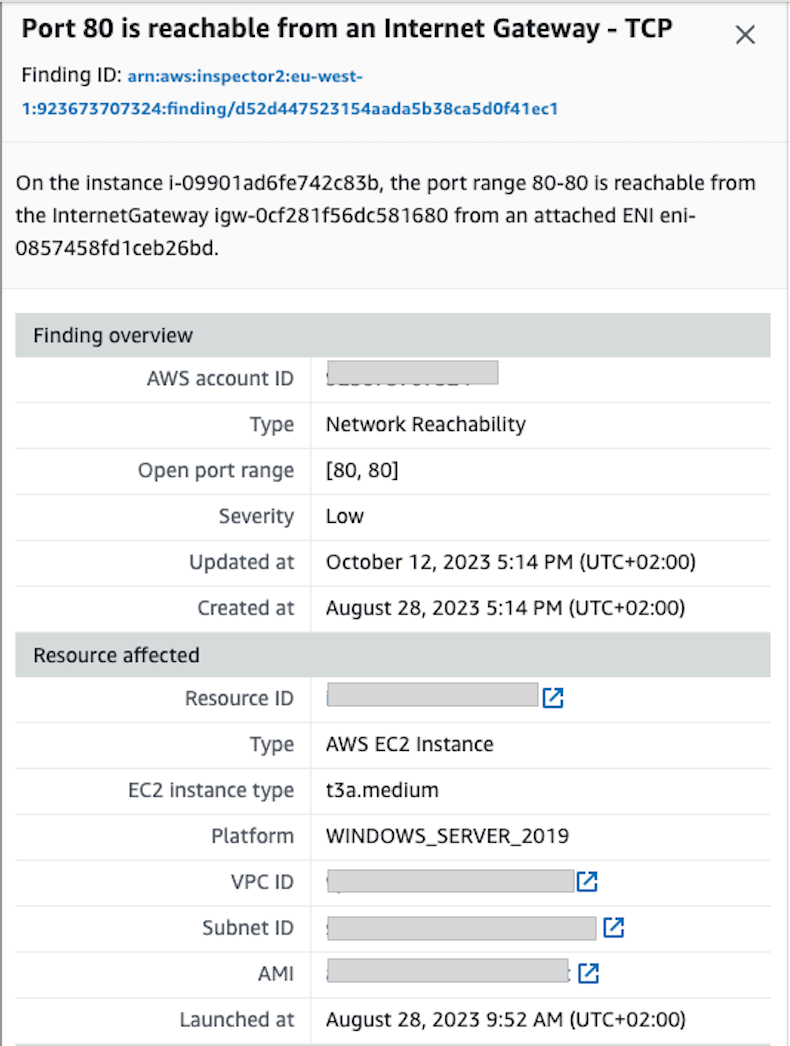
Amazon Inspector automatically discovers workloads such as Amazon EC2 instances, containers, and Lambda functions, and scans them for software vulnerabilities and unintended network exposure. For instance, HTTP service on TCP port 80 open to the world or AWS Internet Gateway.
Our daily approach to each finding starts with analyzing the infrastructure and application impact. Each vulnerability is already scored by the global authorities, but this doesn’t take into consideration the network and application restriction rules. Therefore, we:
- Evaluate the security and compliance of our customer’s AWS infrastructure
- Help the customer to have a clear understanding of the impact the findings have in their environment
- Advise what actions to take
- Mitigate if a fix is not yet available
- Remediate vulnerabilities.
After enabling the Inspector service, every newly created EC2 instance will be discovered and scanned automatically. On the other side, network reachability scans automatically take place every 24 hours.
Example case 1
For instance, CVE-2023-4863 has recently been identified in Windows instances. More precisely, heap buffer overflow in libwebp on Google Chrome prior to 116.0.5845.187 and libwebp 1.3.2 allows a remote attacker to perform an out-of-bounds memory write via a crafted HTML page. (Chromium security severity: Critical).
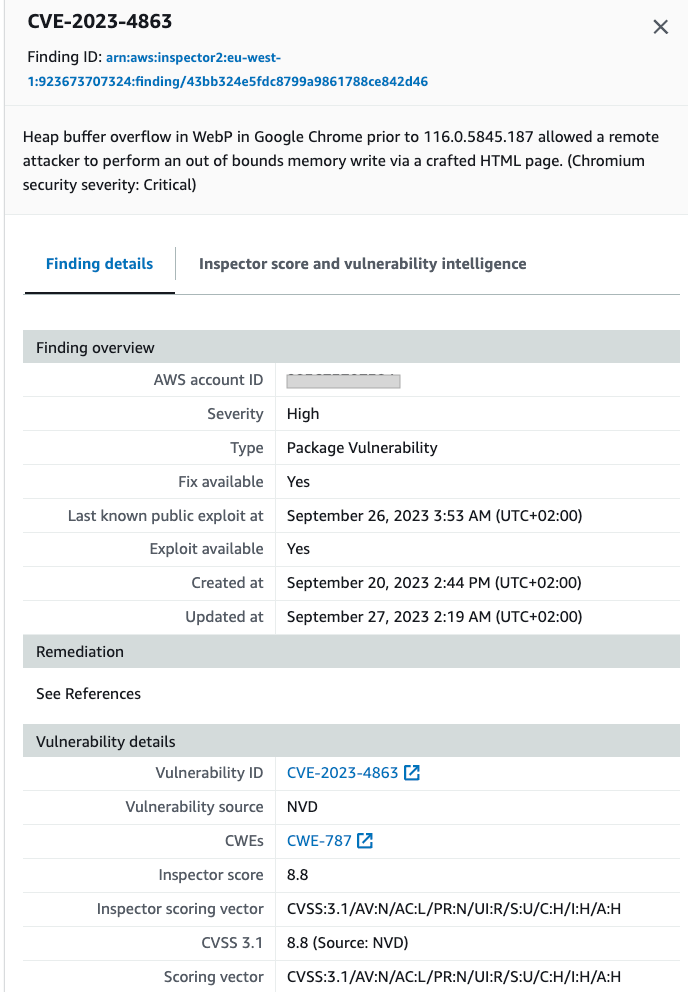
Solution
Since the implementation phase, we have employed SSM to shape the patch baselines, get latest patches automatically and maintenance windows based on customer’s requirements. This ensured automated OS updates and remediation.
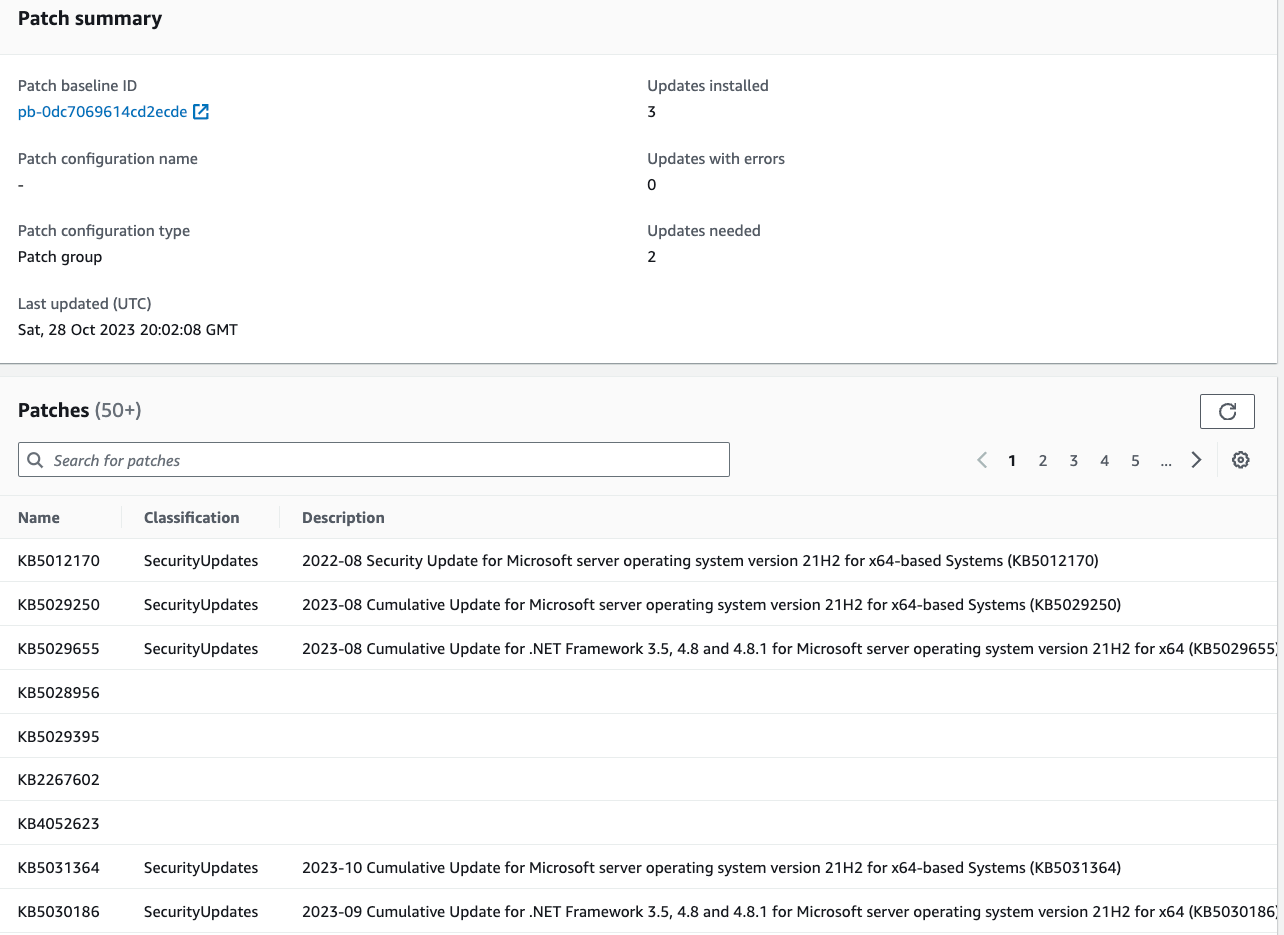
Example case 2
Apart from CVE findings, network scanning are triggered regularly to identify overly permissive rules. For instance, we have been warned in Slack of unrestricted access to ports with high risk. This control checks whether unrestricted incoming traffic for the security groups is accessible to the specified ports that have the highest risk. This control fails if any of the rules in a security group allow ingress traffic from 0.0.0.0/0 or ::/0 for those ports. In order to optimally protect the infrastructure from network exploits, we advised the customer to remove such permissive rules in the security group.
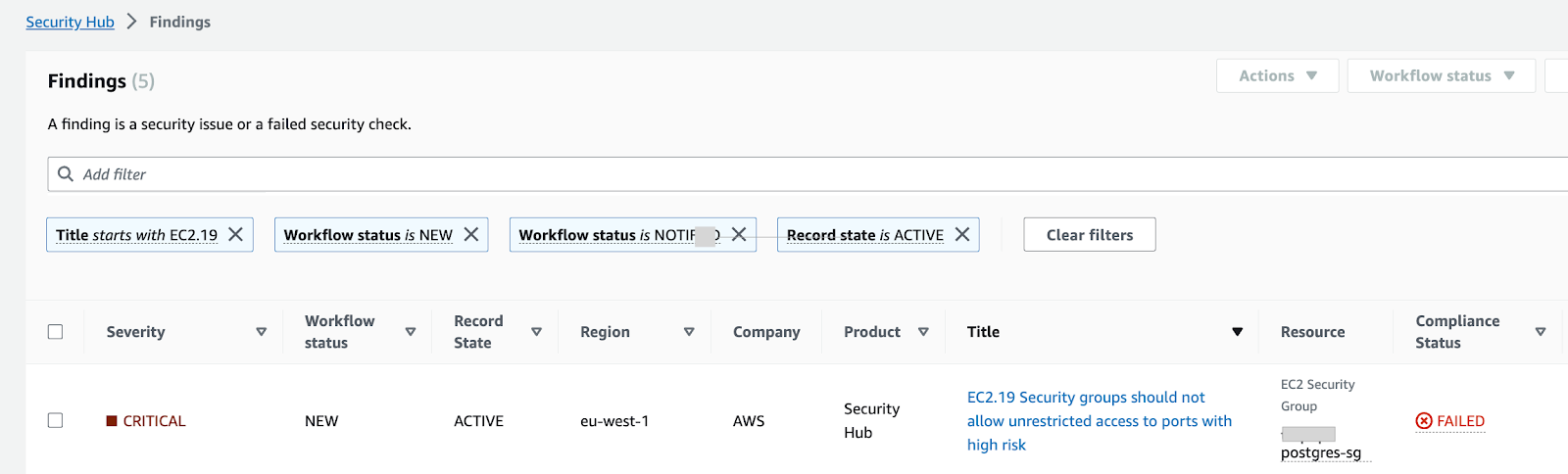
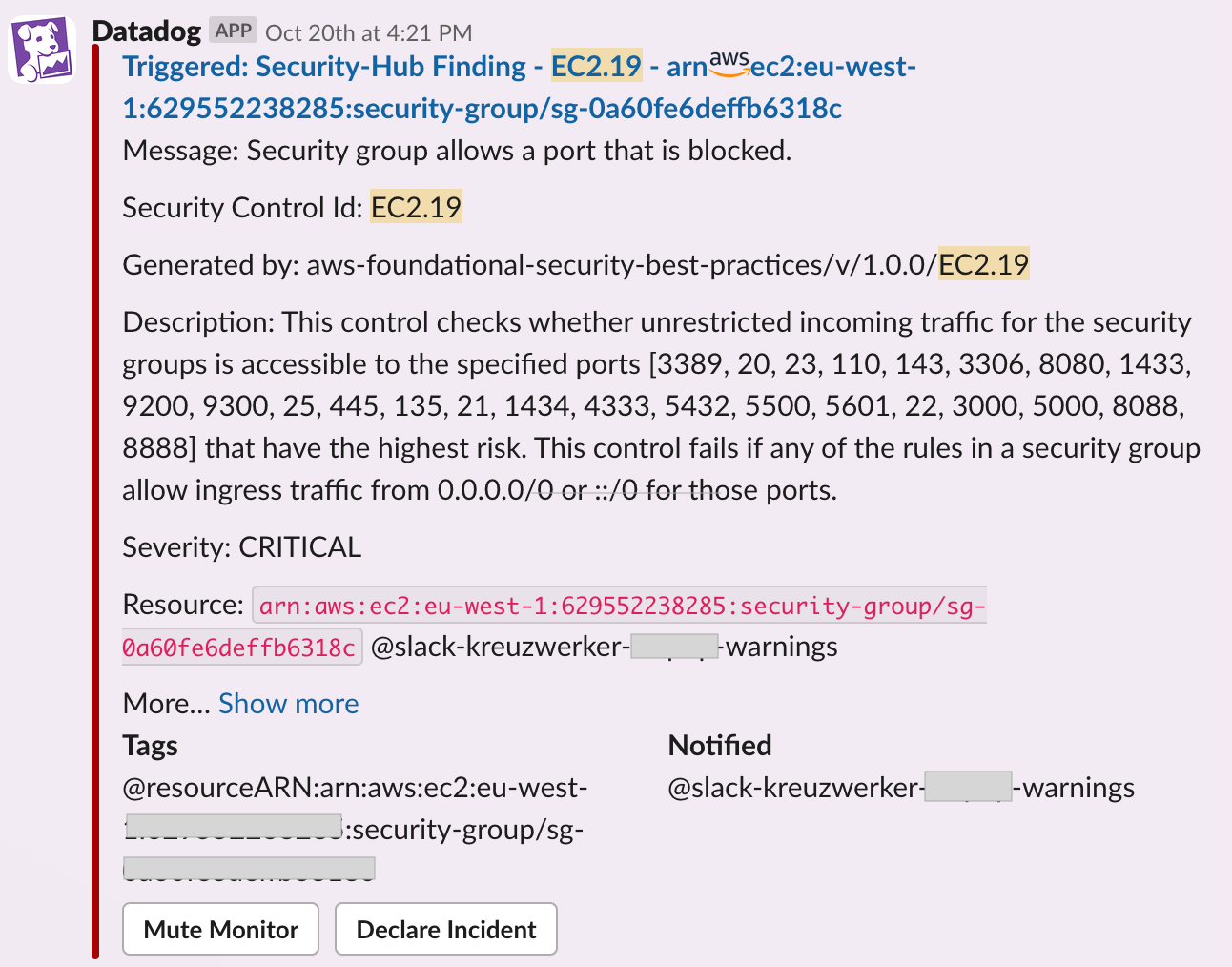
Conclusions
PCG leverages the benefits of Amazon Inspector, Systems Manager, Datadog and Slack to detect, notify and remediate security vulnerabilities.
We combine application security services with Terraform to provide versioning history, quick rollout and rollback. Each instance is automatically detected and scanned. Inspector triggers rescans of the instances just after the installation of new packages or after introducing new CVEs. Last but not least, this solution scans network reachability to identify any insecure port opened to the world, or for example, from the Internet Gateway: