The Compliance Landscape
Understanding the compliance landscape can feel a bit like navigating a labyrinth — or even crossing a mine field if you want to be a bit more dramatic! As such, it’s important to take a closer look at the ever-evolving regulatory requirements, the role of different regulatory bodies, and industry-specific standards.
Multiple regulatory bodies: From HIPAA to ISO 27001
In the seemingly complex terrain of modern compliance, multiple regulatory bodies wield their authority. For example, the Health Insurance Portability and Accountability Act (HIPAA) governs the healthcare sector, the General Data Protection Regulation (GDPR) oversees data protection in the European Union, and the Payment Card Industry Data Security Standard (PCI DSS) ensures secure card transactions.
Meanwhile, in the field of information security, ISO 27001 compliance and SOC 2 adherence are crucial. ISO 27001 focuses on information security management systems, ensuring organizations implement robust security measures. Similarly, SOC 2 evaluates a company's controls related to security, availability, processing integrity, confidentiality, and privacy. Adhering to these standards not only demonstrates a commitment to data security but also enhances trust with clients and partners by showcasing a rigorous approach to safeguarding sensitive information.

The need for compliance standards also isn't limited to a select few, and adherence to these standards also isn't merely a legal obligation and an onerous task that you accept reluctantly; it should be seen as a genuine opportunity for you to build trust with your customers, partners, and stakeholders — each of whom will expect you to handle their data securely and responsibly.
So, where does the cloud come in?
Cloud Solutions for Compliance
Opting for one of the major hyperscalers, such as AWS, Azure, or Google, offers substantial advantages in the realm of cloud compliance. These industry leaders have a proven track record of investing heavily in security and compliance measures. They maintain an extensive list of certifications and adhere to stringent standards, allowing businesses to inherit the compliance status of their infrastructure.
The cloud's scalability and the array of compliance features it offers greatly simplify compliance adherence for customers in the following principal ways:
- Efficiency: Cloud providers invest heavily in security and compliance, relieving customers of the burden of maintaining a secure infrastructure. This allows businesses to focus on their applications and data, streamlining compliance efforts.
- Scaling: Cloud platforms are designed to scale. This scalability extends to compliance efforts. As businesses grow, they can seamlessly expand their compliance practices to meet the evolving needs of their industry.
- Flexibility: Cloud services are highly flexible, allowing businesses to tailor their compliance practices to their unique requirements. This adaptability is crucial as regulatory requirements continue to evolve.

Cost considerations and taking action
Despite these great advantages, businesses should also be aware that maintaining a compliant solution in the cloud may involve additional expenses. While other aspects of migrating to the cloud might save you a lot of money, balancing robust security measures and adherence to standards with budget constraints is crucial for a well-rounded approach.
At the same time, whilst signing up to one of the major hyperscalers is a great step towards regulatory compliance, it’s also important to emphasise that this is just a first step as part of a full compliance strategy. Indeed, this is one of the reasons why an ISO 27001 certification or SOC2 attestation is so important, as they confirm and make sure that a company itself also operates on certain security and compliance standards rather than just ticking boxes.
Tools for Compliance
Likewise, as well as signing up for their services, it’s important that you make full use of all the tools for compliance that the hyperscalers typically provide, including the following:
- Identity and Access Management (IAM): All three major cloud providers offer robust IAM solutions. These services enable customers to manage access to cloud resources securely, controlling who can do what within their cloud environment.
- Data Encryption: AWS, Azure, and Google Cloud prioritize data encryption. They provide encryption services for data at rest and in transit, ensuring that sensitive information remains protected.
- Audit Logs: All three cloud platforms offer comprehensive audit logging capabilities. Customers can track who is accessing their data and systems, aiding in compliance reporting.
- Compliance Certifications: AWS, Azure, and Google Cloud undergo rigorous compliance audits and maintain an extensive list of certifications. This allows their customers to inherit the compliance status of the underlying infrastructure.
Additionally, their scalable and flexible cloud platforms enable businesses to adapt to evolving compliance requirements as the regulatory landscape continues to change. In essence, partnering with a major hyperscaler simplifies the complexities of compliance and empowers businesses to focus on their core objectives.
Shared responsibility model
While the major cloud providers offer a wide range of benefits, it would be a mistake to think that your compliance strategy should begin and end with signing up with a hyperscaler and migrating to the cloud. In the shared responsibility model, cloud providers like AWS, Azure, and Google Cloud ensure the security of their infrastructure.
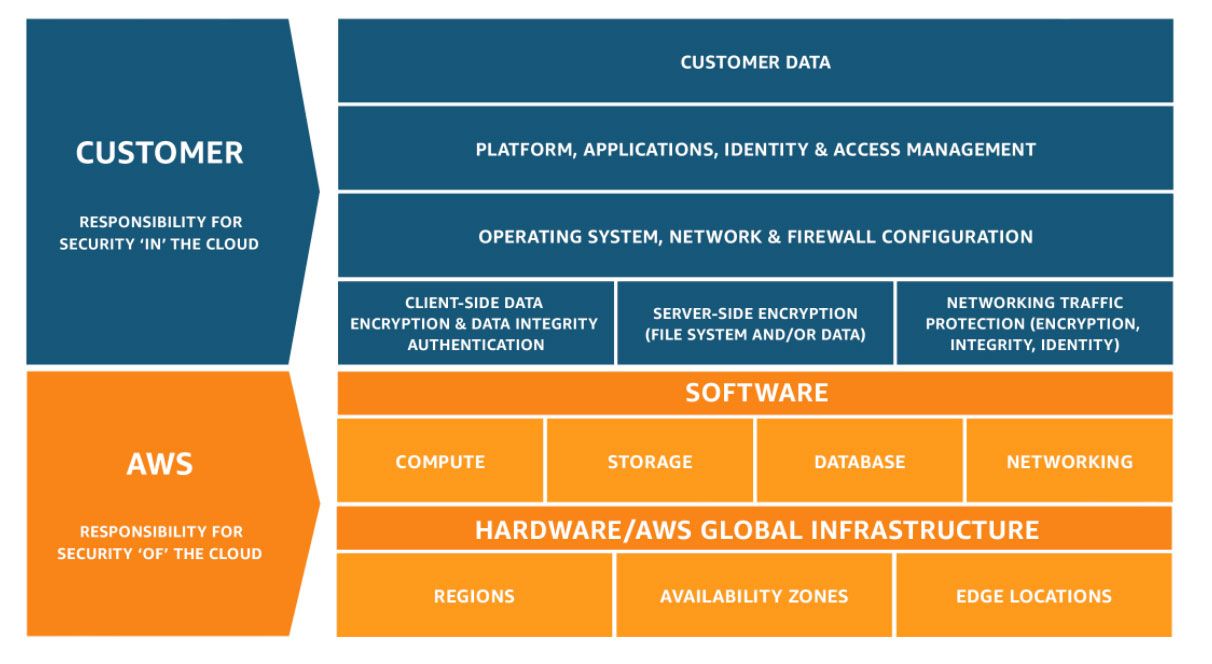
The AWS Shared Responsibility Model
Customers, on the other hand, are principally responsible for securing their data in the cloud and observing a range of best practices. This practical responsibility encompasses several key aspects that organizations need to attend to:
- Use the tools provided: As we’ve mentioned above, the hyperscalers provide useful tools that help greatly with compliance — but it’s your responsibility to actually use them.
- Data Encryption: Customers are responsible for encrypting their data both in transit and at rest.
- Identity and Access Management (IAM): Customers must define who can access what resources, set appropriate permissions, and regularly review and adjust these access controls.
- Security Groups and Network Configuration: Customers need to define and manage firewall rules and network access controls to safeguard their cloud environments.
- Patch Management: Cutting edge software is great and as secure as it gets — but only if it’s kept up to date! Regularly applying security patches and updates is vital to prevent vulnerabilities from being exploited.
- Data Backups and Recovery: You should ensure that their data is regularly backed up and can be quickly restored in case of data loss or system failures.
- Monitoring and Auditing: Organisations need to set up comprehensive monitoring and auditing systems to detect and respond to security incidents. This includes reviewing logs and implementing intrusion detection systems.
- Compliance Adherence: Customers must ensure that their cloud usage complies with relevant regulatory and industry-specific standards. This may involve implementing specific security measures and regularly reporting on compliance status.
- Employee Training and Awareness: In close connection with all the other responsibilities, it’s essential to train your employees on security best practices and maintain a culture of security awareness within the organisation.

In practice, this shared responsibility model means that while cloud providers like AWS, Azure, and Google secure the underlying infrastructure, customers are responsible for securing their data and applications within that infrastructure. It's a collaborative effort to ensure data protection, and customers must be proactive in implementing the necessary security measures to mitigate risks and achieve compliance.
Data Sovereignty Considerations
In a similar way, it's also essential to factor in data sovereignty considerations and businesses must be mindful of where their data is stored and processed, aligning with local data protection regulations. While major hyperscalers invest in robust security measures, it’s important to assess how data sovereignty regulations may affect your compliance strategy, especially when dealing with global data flows.
Compliance in the real world
Now that we’ve understood a bit about the theory and responsibilities, what happens in practice? A good example is the solution we provided for SynapCon, who required a highly secure and stable platform for their clinical trial data management software, "easyTMF". This software handles sensitive personal and health-related data of clinical trial participants. By choosing Amazon Web Services (AWS) for the cloud infrastructure, SynapCon ensured that their platform was not only secure but also compliant with GDPR regulations. AWS provides robust security features and compliance tools, which help in meeting the strict data protection requirements mandated by GDPR.
In the medical sector, cloud services aid in ensuring compliance. For instance, consider a healthcare organization leveraging a secure cloud platform for storing patient records. The cloud provider ensures encryption, regular backups, and stringent access controls, meeting industry standards like HIPAA (Health Insurance Portability and Accountability Act). This centralized cloud storage allows for seamless auditing, easy tracking of data access, and swift updates to compliance protocols across multiple locations or healthcare facilities. It also facilitates adherence to evolving regulations by integrating automated compliance checks and updates into the system, ultimately ensuring patient data security while meeting regulatory requirements.
Securing Your Cloud Future: A Compliance-Driven Partnership
Even with a couple of short examples, we can start to see how the cloud can support and shape your approach to compliance. While it can be daunting at the outset, the path becomes much clearer with the right cloud solutions provider by your side. Major hyperscalers like AWS, Azure, and Google Cloud offer not just a secure and compliant infrastructure but a wealth of tools and features that simplify adherence to even the most intricate requirements.
While the cloud providers take care of securing their infrastructure, customers also play a vital role in ensuring the protection of their data within it. In a world of evolving digital landscapes and stringent regulations, this partnership is the key to safeguarding your organization's future.
Further Reading
- Security and compliance - Overview of Amazon Web Services
- Google: Cloud Compliance & Regulations Resources
- Cloud Security and Privacy: An Enterprise Perspective on Risks and Compliance
by Tim Mather et al.
- Understanding ISO 27001: The 2024 Updated Guide for Beginners
Unlock the Power of Secure Cloud Compliance
Ready to fortify your cloud compliance journey? Our ISO 27001 Compliance as a Service is designed to seamlessly integrate with your cloud infrastructure, ensuring your data protection strategies meet the highest standards. Contact us today to embark on a compliance journey that guarantees safety, flexibility, and peace of mind.

